OSINT
Don’t Get Caught
Description: it looks like an individual going by the handle
@_simpleadamhas been caught spreading a secret link to the CyberX group without permission! Your task is to trace his social media just by googling really, and find out the flag from his account :b
So here what you need to do is investigate any account that is linked to the alias @_simpleadam
We can try a simple google search for this!
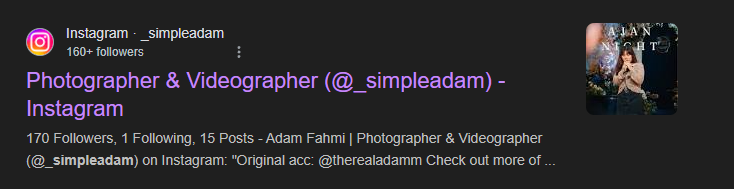
Now as you can see the first result shows that the account belongs to an instagram account. Now it’s time for you to investigate it even more!
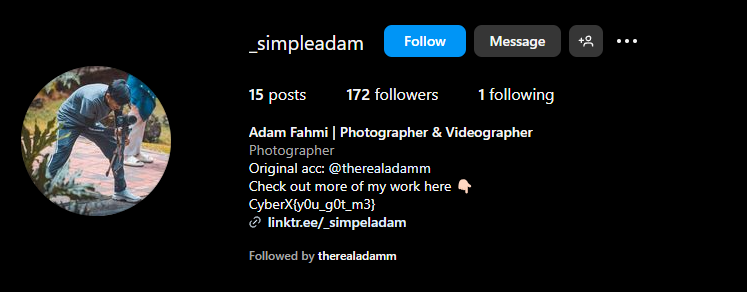
As you can see in the bio there is the flag! CyberX{y0u_g0t_m3}
Jangan Pandang Belakang
Description: Near UTM’s Makmal Einstein, there’s another eerie place… Just a short walk away, this building is known for strange events. People hear footsteps in empty rooms, see shadows in glass reflections, and experience random equipment failures. Isolated and dimly lit, it leaves visitors feeling watched. While Makmal Einstein is spooky, this place may be where the real mysteries are…
The first thing that you need to do is find out the nearest building to UTM’s Makmal Einstein, but how? You can try Google Maps.

Here as you can see the nearest building that is shown on the map is P18. Now investigate more information about that building!
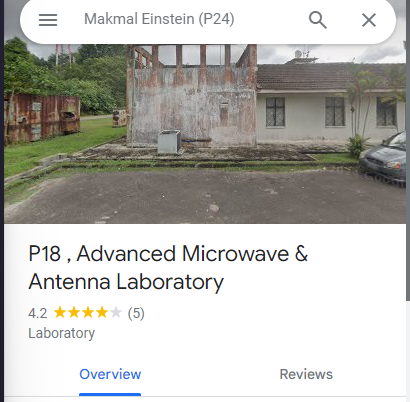
Notice that there are 5 reviewers… weird eh? Try to check it out
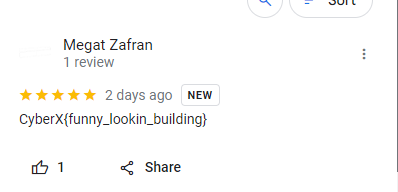
Then, there is the flag lol CyberX{funny_looking_bulding}
Web
Common Developer Oopsies 1
demo
Description: They left confidential credentials on their website or exposed them publicly on the internet.
Website: https://joboncampus.com/login.php
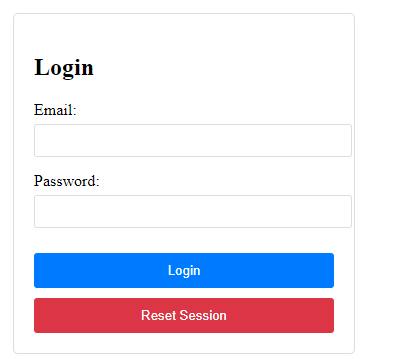
So the first clue is that the developer left some credentials on the website… let’s to see if there are any comments left on the page..?
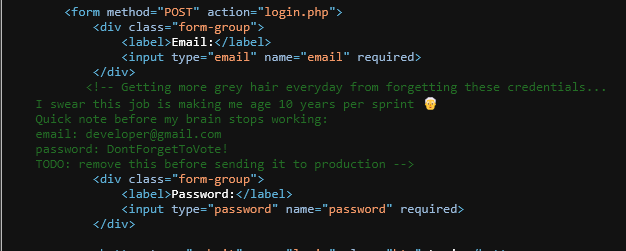
There it is now let’s try to login using the credentials left carelessly by the developer
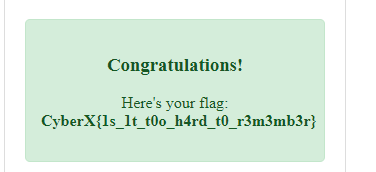
CyberX{1s_1t_t0o_h4rd_t0_r3m3mb3r}
try me
website: https://joboncampus.com/upgradedlogin.php
Common Developer Oopsies 2
Demo
Description: Insecure Direct Object References (IDOR)
Website: https://joboncampus.com/profile.php
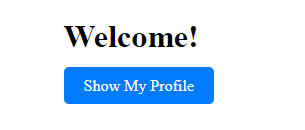
First looking at the website there is a button show my profile.
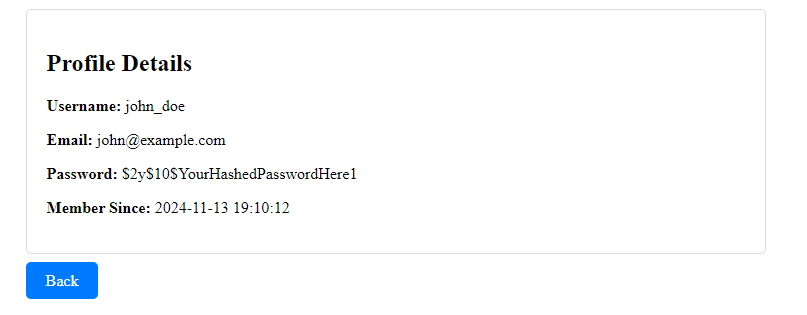
After clicking it, it shows the details of the profile.

Apart from that url updated with a parameter id with the value of 1
To determine if the website is vulnerable to IDOR(Insecure Direct Object Reference) attack try to change the value of id and see if the profile changes.
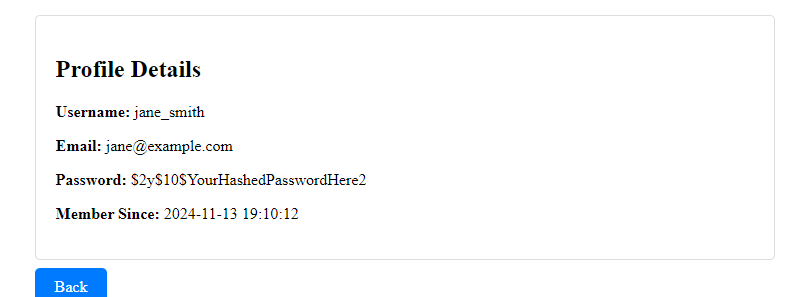
As you can see it changes to another profile :]
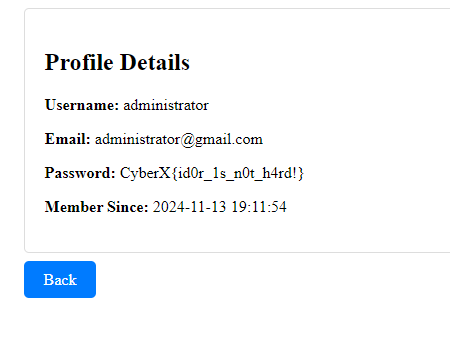
So now your goal is try to find any other account that is potentially might be related to the administrator. Let’s try to change the id into 4

There goes the administrator account!
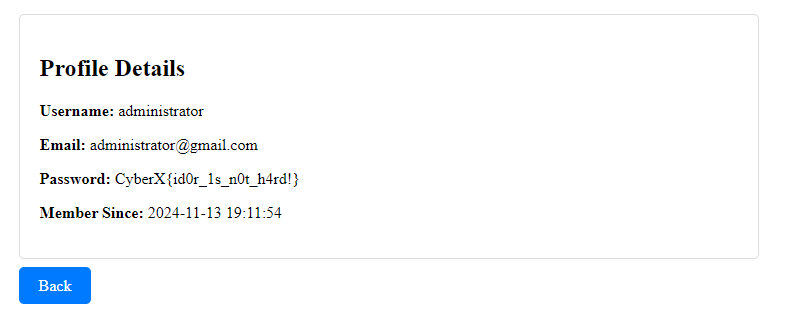
CyberX{id0r_1s_n0t_h4rd!}
try me
This challenge is the same as before, but the id value is encoded with md5 hash.

How do I identify if it’s md5? Well if you’ve tried a lot of CTF challenges, it is easy to recognize what kind of encryption the ciphertext is.
For beginners you can try this cipher identifier https://www.dcode.fr/cipher-identifier!
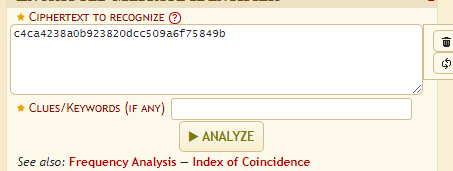
Insert the hash and press analyze, now take a look at the left side of the UI. It will show you what kind of encryption it is. Looks like md5 tho.
So in previous cases, the administrator account id is 4, so lets try to encode 4 with md5 and use its hash as the id value. Yes, you can use https://www.dcode.fr to encode the value 4 to md5, or you can try cyberchef works too.
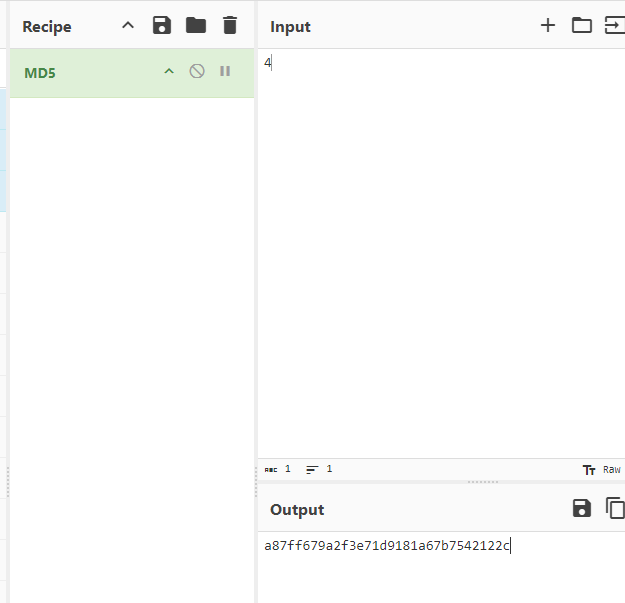

There goes the flag :], yes its the same as the previous one.
CyberX{id0r_1s_n0t_h4rd!}
Common Developer Oopsies 3
Demo
Description: Insecure Direct Object References (IDOR) - Through Cookies
Website: https://joboncampus.com/biskut.php
So here if you take a look at the cookie by going to the developer tools.. inspect > application > find cookies tab > find the website > now take a look at user_id name and its value.
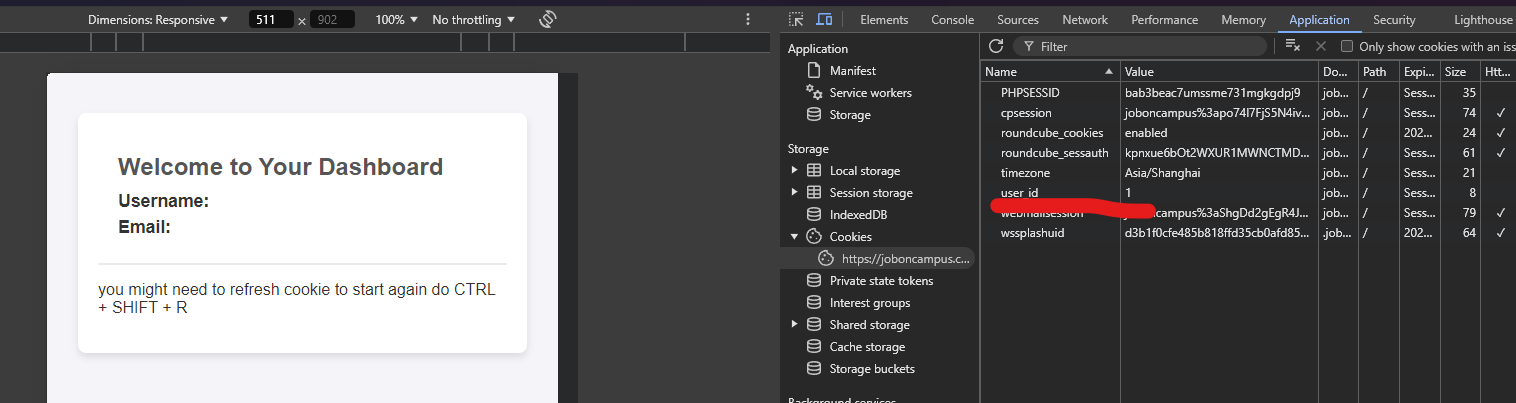
Try to change it, then press somewhere on the webpage to make sure the value is set to the one that you changed, in this case lets try 4 and refresh the page!
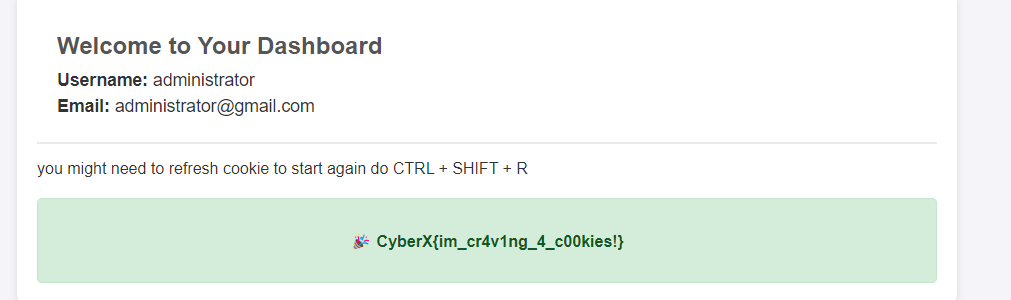
CyberX{im_cr4v1ng_4_c00kies!}
try me
Website: https://joboncampus.com/upgradedbiskut.php
Same method, here if you take a look at the cookie by going to the developer tools.. inspect > application > find cookies tab > find the website > now take a look at user_id name and its value.
Now instead of a single decimal value, it is encoded in md5 hash, so try to encode the value 4 with md5 hash and refresh the page!
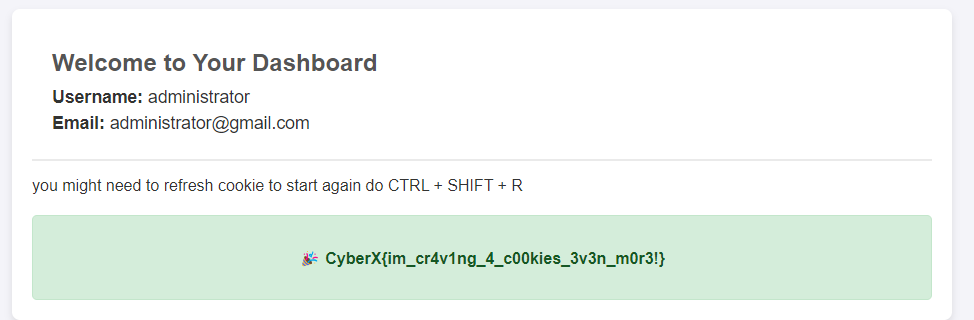
CyberX{im_cr4v1ng_4_c00kies_3v3n_m0r3!}
Forensic
So, for the digital forensic challenge, we were given a zip file containing 1 jpg named doge and 1 png file named capybara.

So, the first step in the challenge is to try opening it (remember if you cannot open the file then there is no forensic to be done). And as to no one surprise, you cannot open both of the files :).
Well, I know that I said if you cannot open it, you cannot forensic it, but you can still try a few stuffs. One of them is checking the metadata of both files.

While this step can be discarded since none of the exiftool online is giving the correct output unlike the one in linux, this step gives us few valuable information, for example from the modification date/time section we can that capybara.png was modified first, then only doge.jpg was modified.
With this info on the timeline of the files, we can do the forensic on the capybara.png file first before moving to doge.jpg. Well, we could also see that capybara.png has extension of png but exiftool is giving us the file type of jpg. This leaves us with 2 options, either the extension is changed or the magic bytes is changed.
So, let’s try the first option, change the extension and try to open it.
Given this error, it is most likely the second option. Let’s open Hexed.it for further inspection.
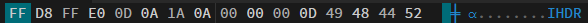
This is the output we get (we get more, but this is what we are interested in). From this we can see 2 interesting things, the first 4 bytes FF D8 FF E0 is the magic bytes for jpg but the IHDR is something shown for png file. So, either the author changed the file signature or he changed the JFIF(JPG) into IHDR. Let’s try changing the magic bytes into png one and try it first.
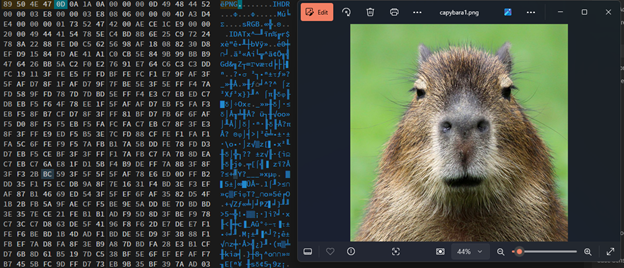
Looks like the author just changed the leading bytes. But remember they could also change the IHDR just to mess with us. Looking at the png, it is just a picture of capybara and nothing interesting is there. Let’s try AperiSolve and see if it could find something for us.
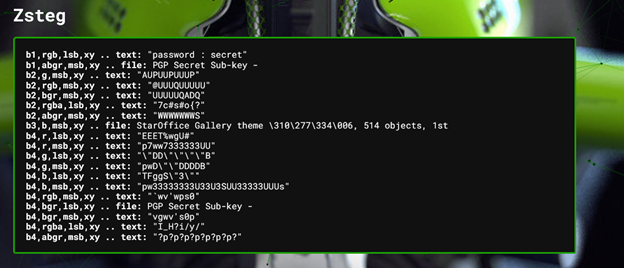
Hmmm there is a text behind the png with telling password is secret. Maybe it is for the other photo or it could also be for this photo. Well it is better to leave no stone unturned so let’s add the password in AperiSolve and try for this png too.
This is where you put the password, just below the main page where you submit the png too. But to no luck, it seems that the password is for the other picture and hopefully we are done with this picture. Let’s go to doge.jpg now.
Try to open it in hexed.it just like what we done for capybara.png.
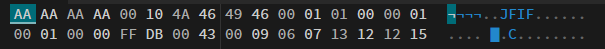
Looks like the author just changed the leading bytes here lol. Change it to FF D8 FF E0 and save it.
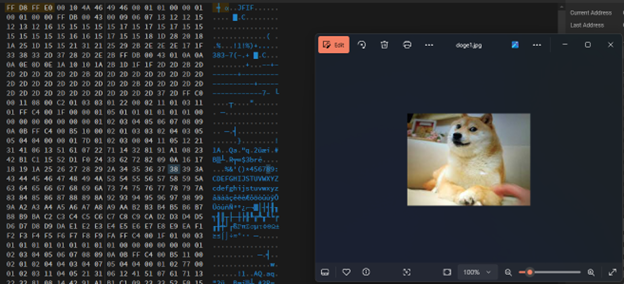
Now let’s put this on AperiSolve with the password we got from capybara.png (secret).
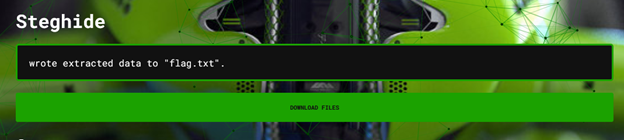
And voila, steghide find a flag.txt behind the doge.jpg, let’s download this and hope this is our flag.

Unzip the file and access the flag.txt.
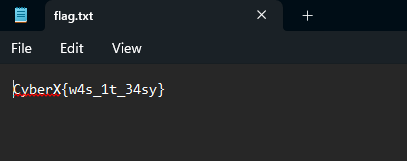
And that’s it. The flag is CyberX{w4s_1t_34sy}
Hope you guys enjoy the challenge, if you guys have more questions can contact me via discord : PLSSKY