Config
There are 3 types of setup that you can use:-
- Source Code
- Docker
- Virtual Machine
In my case I’m going to use docker.
First, clone the lekir docker repository.
https://github.com/firdauskhairuddin/lekir-docker/tree/main
After that, you need to build the docker and also run the service.
1 | docker compose build |
Now you should be able to check out the vulnerable website on your localhost on port 1337.
http://localhost:1337
Login Page
So first of all, you will be given a login page, right before you have the access to the dashboard.
I was confused at first, I thought the developer forgot to give the creds, but then I was told that you need to find the creds by yourself.
Lets try to brute force the login page. Oh I also got a heads up that the username is admin from this image in its GitHub repo.
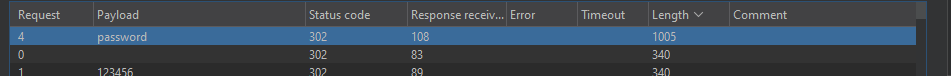
Most of the wordlists I use is usually from this repository. Turns out that the password is literally password.
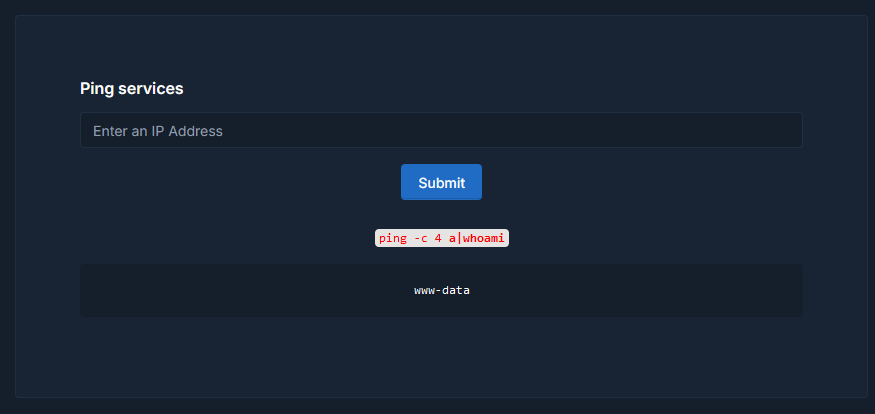
Command Injection Vulnerability
Here on the dashboard page you can choose any type of vulnerability you are interested, for me I think command injection would be fun to try.
Low
Here is the source code, it will basically use the $_POST variable value that is retrieved from ip and assign it to another variable $target. Later on it will find out if the server is Windows/Linux and execute a ping command.
1 |
|
To bypass this all you need to do is inject the ; inside the ip value like-so google.com;.
Now you will have the ability to add a second command right after ;. For example:-
1 | a; whoami; |
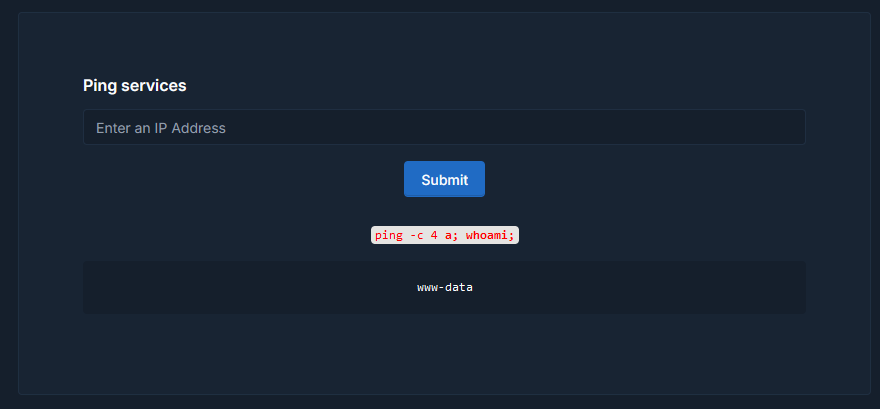
Therefore the command that will be executed is:-
1 | ping -c 4 a; whoami; |
Medium
The source code is almost the same except for a blacklist function is added. Any characters of && and ; will be removed.
1 |
|
To bypass the blacklist function there is other operator that you can use. Referring to PayloadsAllTheThings repo, the other commands that can be used for chaining is:-
||will execute the command only if the first command fails&execute command in the background|takes the output of the first command and uses it as the input for the second command
So in this case || seems viable for injection.
1 | a || whoami; |
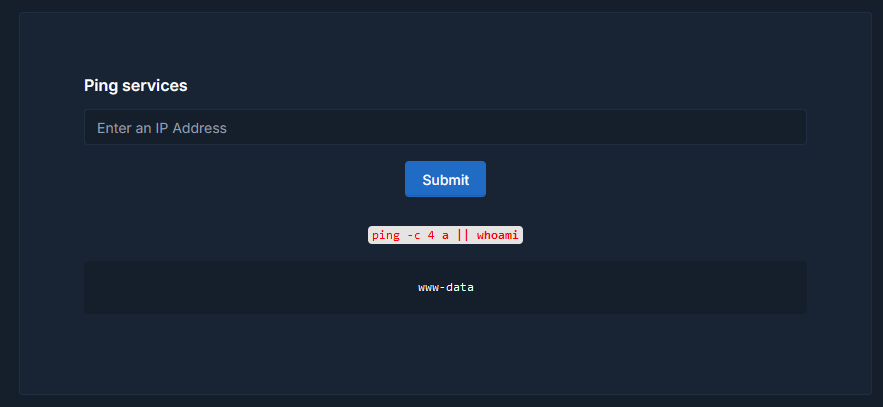
Therefore the command that will be executed is:-
1 | ping -c 4 a || whoami; |
High
Same functionality of source code, however the list of blacklist character expands.
1 |
|
Not sure if this is the intended way to solve this question but I realized that one of the blacklist array value | is considered the same as |. Therefore, if I try to inject |test it will not be removed by the function.
1 | a|whoami; |
Therefore the command that will be executed is:-
1 | ping -c 4 a|whoami; |