This is one of the most memorable CTF events for me since I’ve decided to bring along a couple of my friends from SECRH: derf, Arif, akim, Rohman, and Hisyam.
I’m pretty sure they were traumatized by how hard it is to solve the questions.
PS - I didn’t know it was going to be that hard since the challenges at rAKSASA were too damn easy compared to rENTAS.
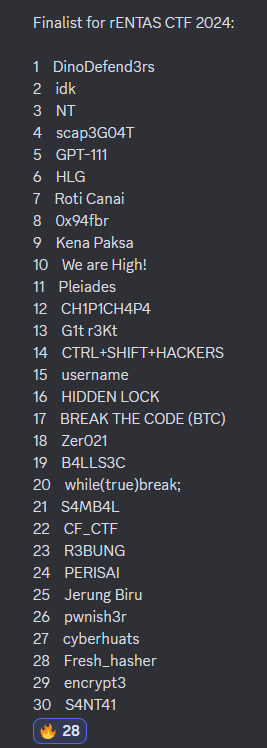
Luckily, we managed to get into the top 30 thus bringing us to the final stage of Rentas.
OSINT
Medellin Cartel + Cali Cartel
This is one of the most complex OSINT challenges I’ve encountered, so it gives you this picture from the Medellin Cartel Challenge.

Doing some reverse image search tells us that the source of the image is a Reddit post on r/Narcos.
So I searched the keyword RWSC in the subreddit, and it accidentally gave me the second challenge flag instead of the first one. LMAO
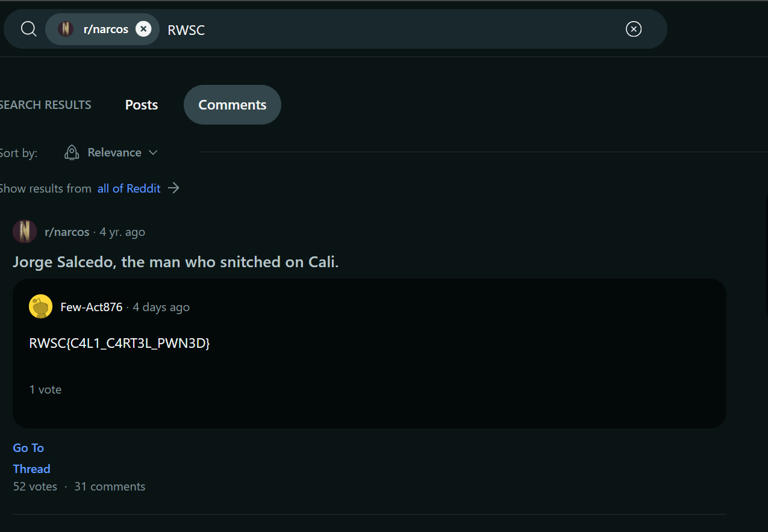
flag RWSC{C4L1_C4RT3L_PWN3D}
I didn’t solve the first part, though, which is frustrating.
DFIR
Last Hope
Question: flag = RWSC{wifipass}
Going into the challenge, they first gave us a .cap file containing raw data and metadata captured over a network transmission.
When I got the cap file, I first tried to find out the protocol of the packets using Wireshark, which is identified as 802.11.
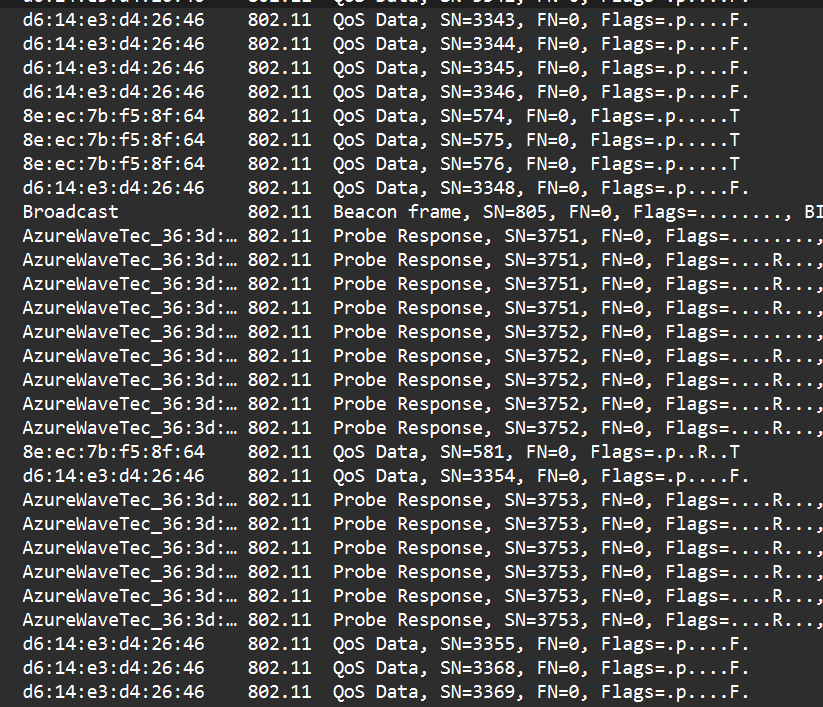
Here, I find out that one of the packets is vulnerable to brute force that will eventually show the wifi password.
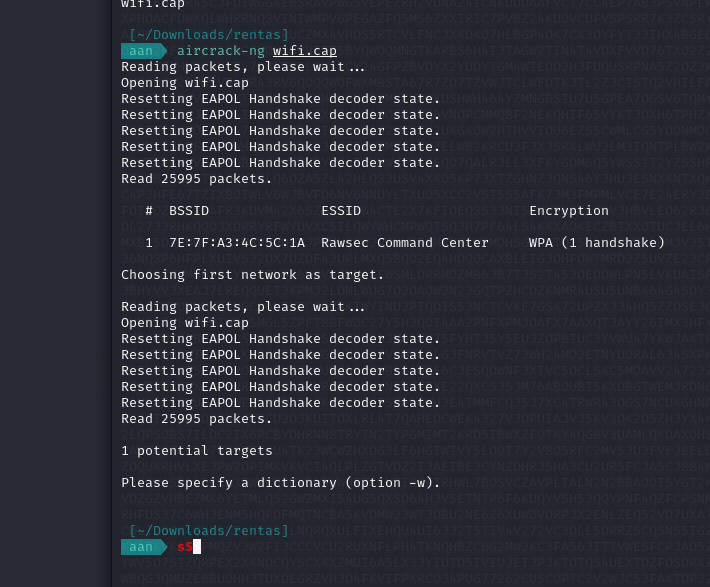
After performing the brute force using wifite.txt wordlist, the password shown as anonymous
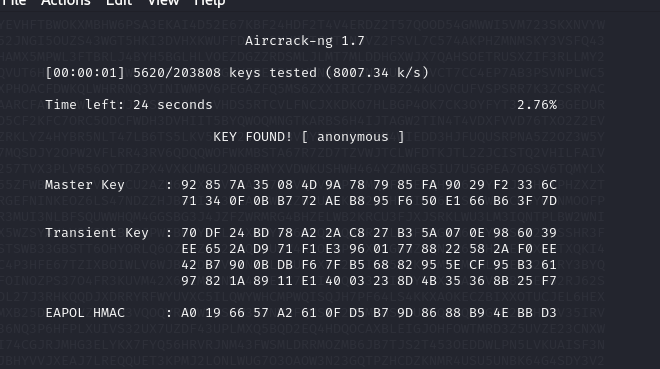
flag RWSC{anonymous}
Web
Lah Itu Je?
First, when we look at the website, we are presented with a login form.
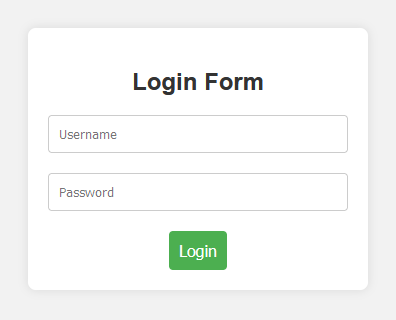
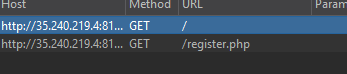
Intercepting it using burp suite shows that there is another path called register.php
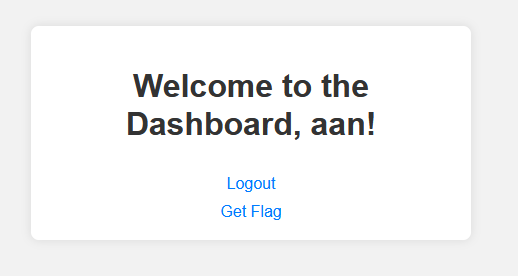
After creating an account and logging in, it redirected to dashboard.php; right after that, pressing the get flag will redirect you to another page, which is flag.php
We did this by checking the page source and looking at script.js; the js file is obfuscated inside the file. Therefore, we need to use the javascript deobsfucator
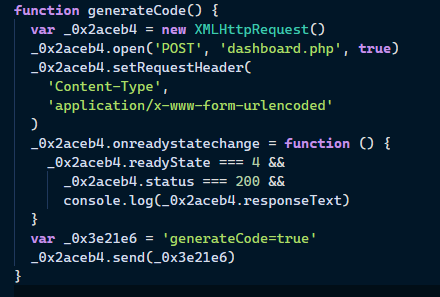
Next, we just run the generateCode() function using the console, then it will alert the code; however, making a POST request with the code doesn’t provide the solution, and another alert box comes out
After banging my head against the wall for 4 hours straight, I decided to wait for the clues.
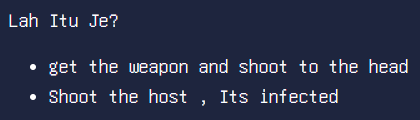
Here, it states to shoot to the “head.” I guess we need to change the request from post to head.
Nope, I was wrong; moving on to another clue, shoot the “host.”, here I changed the host header to localhost, and it provided a strange response.
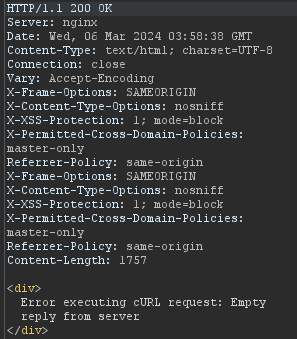
200 OK and Error executing curl request: Empty reply from server
Hm, it is clear that it is a vulnerability of SSRF via Host Header
Therefore, all I need to do is create my domain using the request in the website and inspect the request
Lastly, decode the flag from Base64
flag RWSC{b045887cbadfda25b29db243a18de38cb1cbfb14}
Misc
Hidden Discord
Question: Starting point: (https://discord[.]gg/7aMtftbDY4)
Disclaimer: I and I was trying to solve this challenge until 3 am but still have no clue where the flag is hiding except for three flags, which is the icon of the server, voice channel message, and the event description
But thank god rohman (nenowo) managed to solve it the next day while I was sleeping
First what he did was he went straight into the voice channel and click the chat button
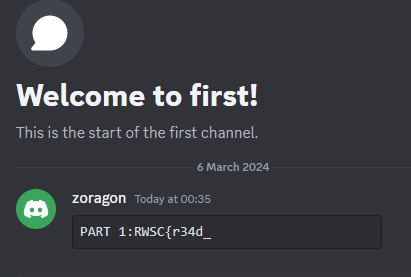
Next, he takes a look at the event description
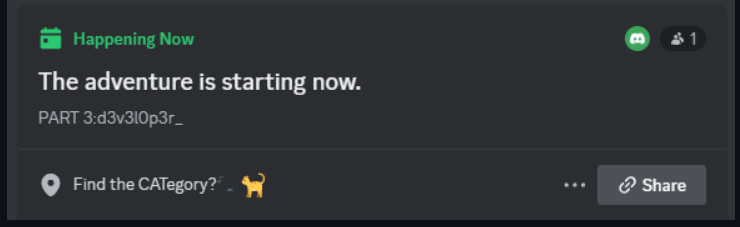
Later on, he discovered that to find out the rest of the flags, you need to make use of the BetterDiscord application and use the showhiddenchannels plugin
After setting it up, go straight ahead into the server, and voila, it shows the hidden category
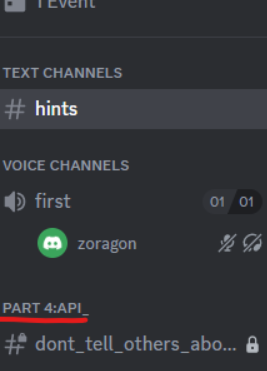
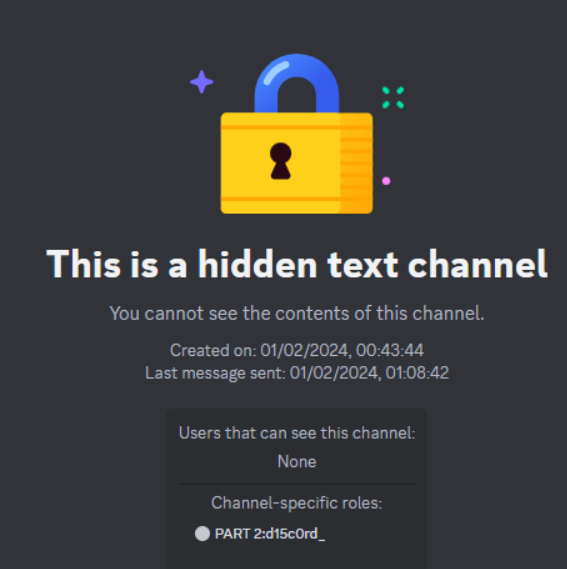
Later on, there is also a hidden channel that provides another part of the flag which is located at the role
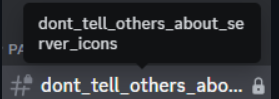
The hidden channel name also implies that there is a part of the flag at the icon of the server
To grab the server icon, here is what he did: first, he went to Discord Web and then to the element pane.
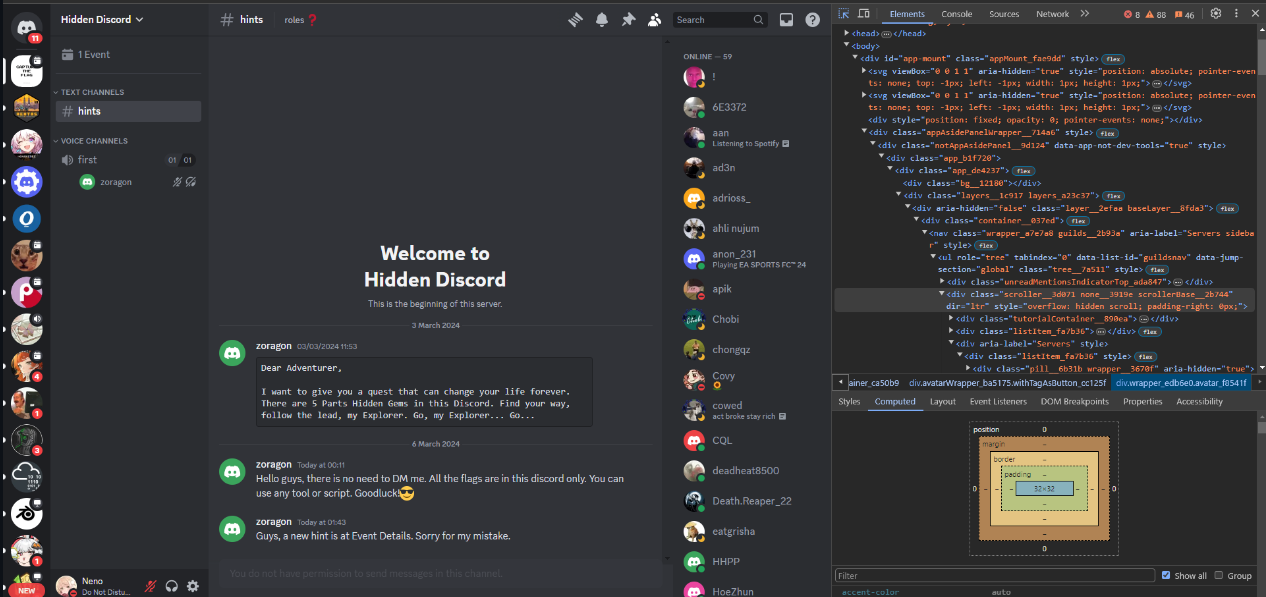
Then he copied the src of the image
Even though he managed to grab the image now, he encountered a new problem: the image wasn’t that clear since the gray text was blurry

So, change the? size in the URL to 4096.
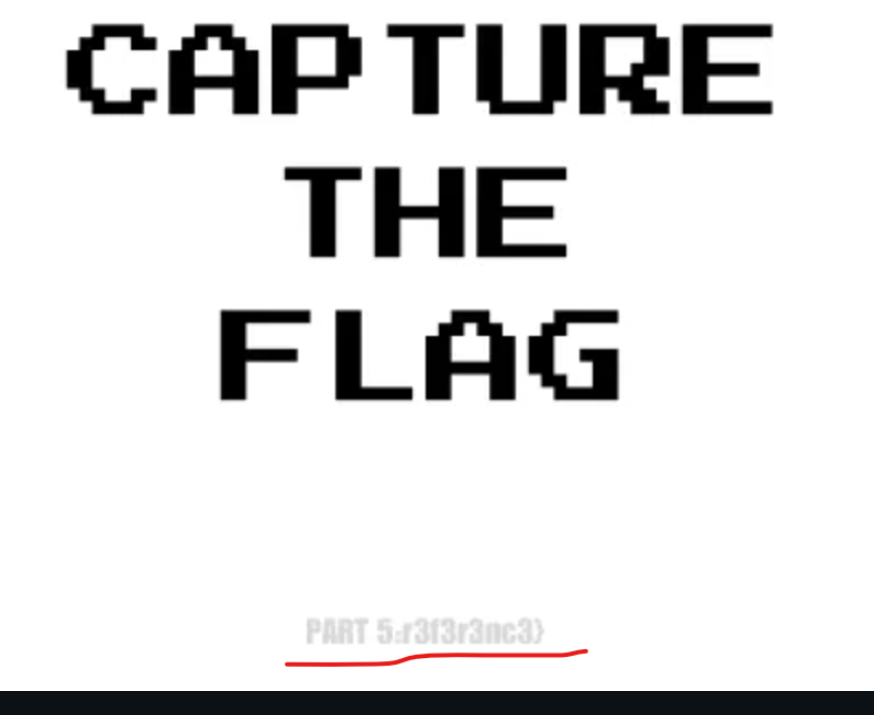
flag RWSC{r34d_d15c0rd_d3v3l0p3r_API_r3f3r3nc3}
Crypto
Roundandround
Disclaimer: This challenge is also solved by Rohman (nenowo)
Upon downloading the cipher2.txt file, here is what we got 2126226{19122929121712_6121911821_26422_842928}
Since the first couple of flag formats must be RWSC letters, it is quite obvious that we need to use number to letter decrypter
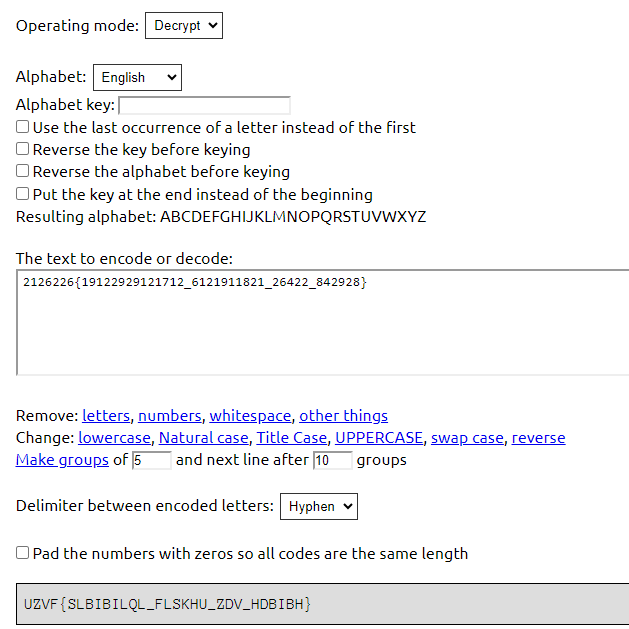
We get UZVF{SLBIBILQL_FLSKHU_ZDV_HDBIBH} as a result
Okay this part I have no clue how he did it, but after reading the solutions, the text was encrypted using Pizzini Cipher, and this is how he managed to find out that was the solution
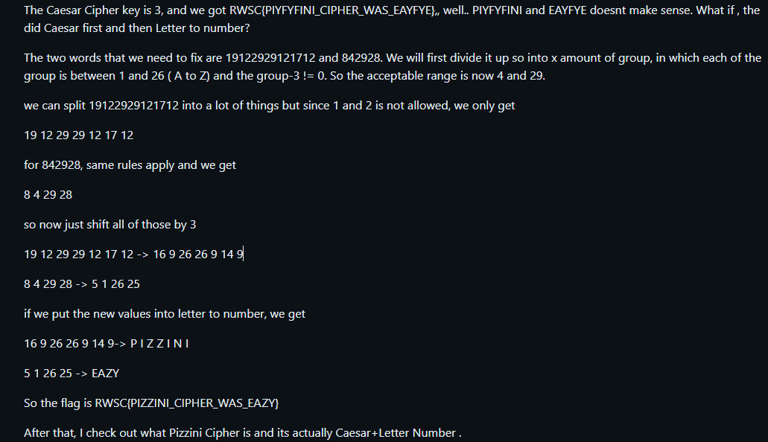
flag RWSC{PIZZINI_CIPHER_WAS_EAZY}