Challenges from LA CTF hosted by ACM Cyber at UCLA and Psi Beta Rho
Web
Terms and Conditions
Welcome to LA CTF 2024! All you have to do is accept the terms and conditions and you get a flag!
To press the accept button in step 1, you need to resize the screen so that it will let you open the inspection panel (there is a specific size that will trigger the “NO CONSOLE ALLOWED”)
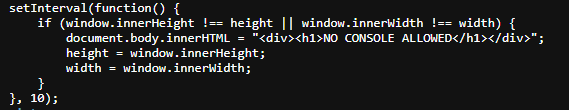
This code checks if the height of the browser window (window.innerHeight) is not equal to the variable height, or if the width of the browser window (window.innerWidth) is not equal to the variable width. If either of these conditions is true, the code inside the curly braces will be executed.
Once you manage to do so, grab the button’s ID—in this case, it is “accept.” Go to the console and click the button with this command. accept.click()
flag lactf{that_button_was_definitely_not_one_of_the_terms}
Misc
Infinite Loop
I found this google form but I keep getting stuck in a loop! Can you leak to me the contents of form and the message at the end so I can get credit in my class for submitting? Thank you!
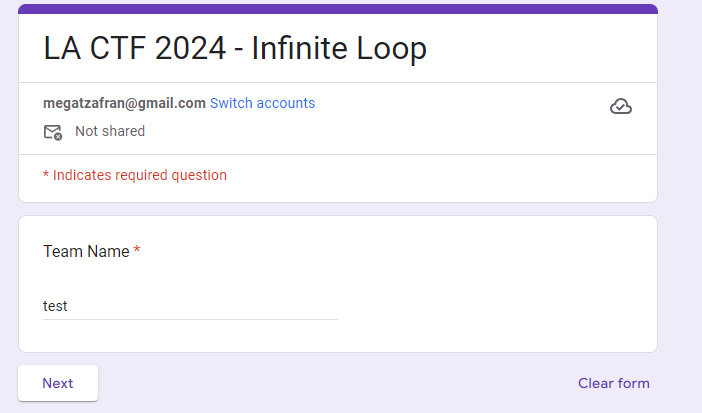
Looking at the Google form is presented with team name questions, and after pressing next, it will repeatedly ask the same questions, which is 1+1. If you insert your answer and press next, it will ask the same questions repeatedly.
Like always, my approach here is to go to the inspect element, CTRL+F, and find the flag last.
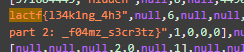
As you can see, it is separated into two parts.
flag lactf{l34k1ng_4h3_f04mz_s3cr3tz}
Reverse Engineering
I swear I knew what the flag was but I can’t seem to remember it anymore… can you dig it out from my inner psyche?
We were given a file, so I first tried to find out what type of file it was.
Huh, so it is an ELF 64-bit. Therefore, we can reverse engineer it using Ghidra and take a look at the decompile panel.
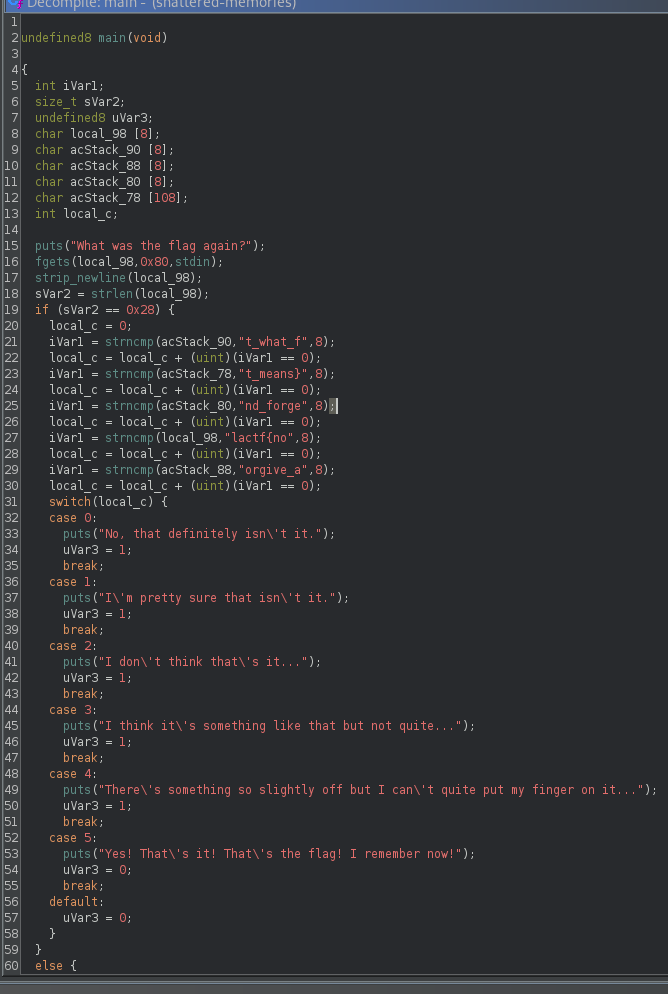
If you look at the code above, it compares the user input with the specified flag. Therefore, we need to reconstruct it until it provides the output telling us that we have already got the flag
flag lactf{not_what_forgive_and_forget_means}
Steganography
NOTE: Unfortunately we goofed up and uploaded the wrong file. As it’s too late into the CTF to fix, we will be leaving the challenge as-is. Yes, you can just hear the flag in the audio file directly. I can’t figure out what my friend is trying to tell me. They sent me this recording and told me that the important stuff is at 40 kHz (??? what does that even mean).
This is my very first challenge that is related to audio steganography, it is really easy just hear the NATO Phonetic Alphabet and translate it into a flag
flag lactf{c4n_y0u_plz_unm1x_my_s1gn4lz}